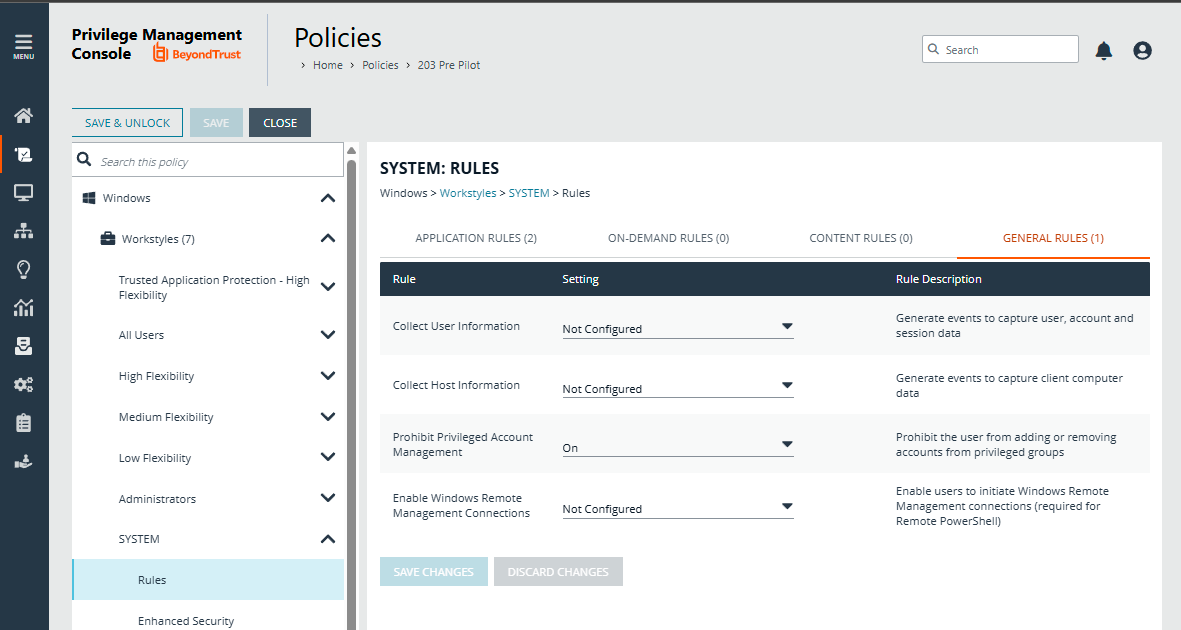
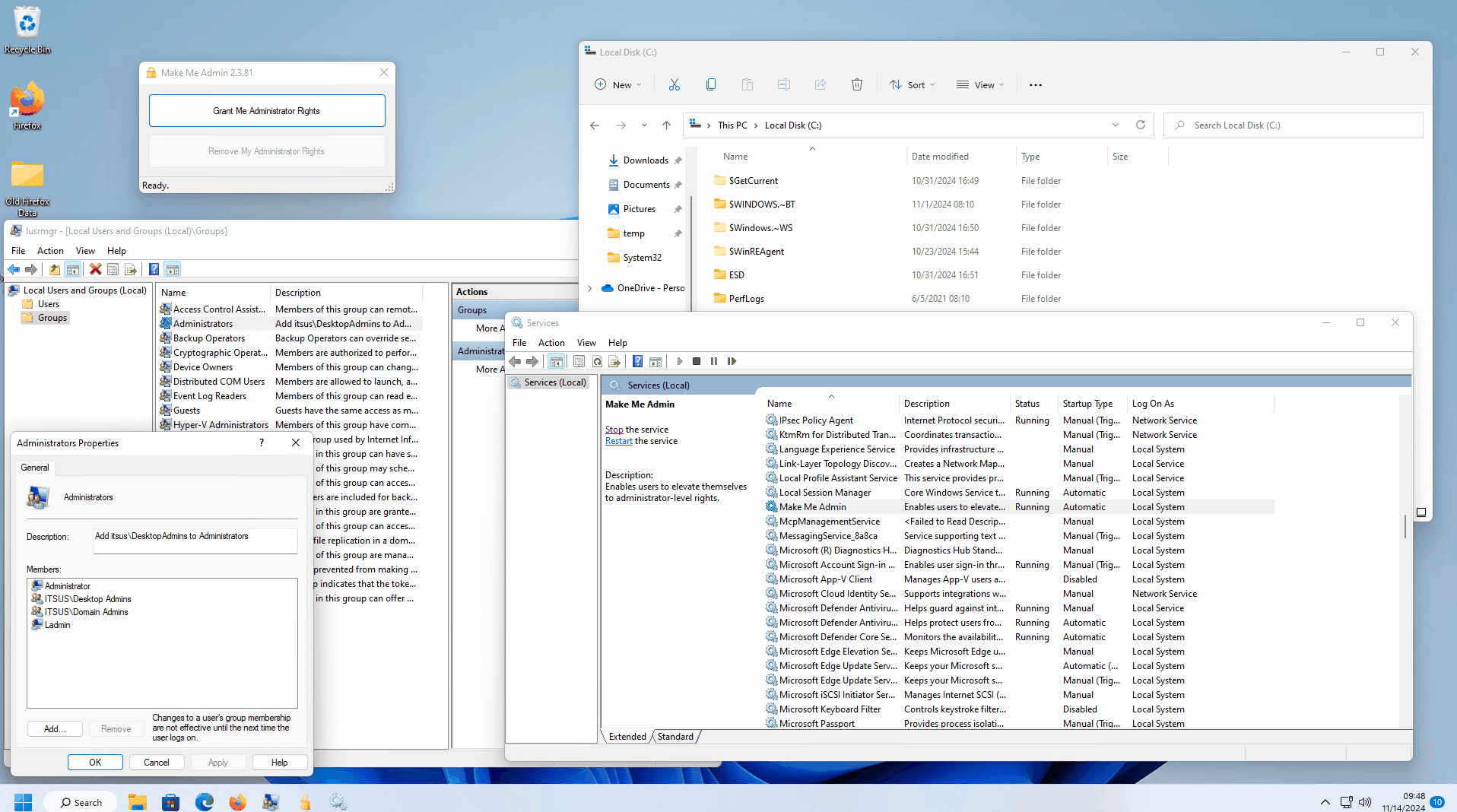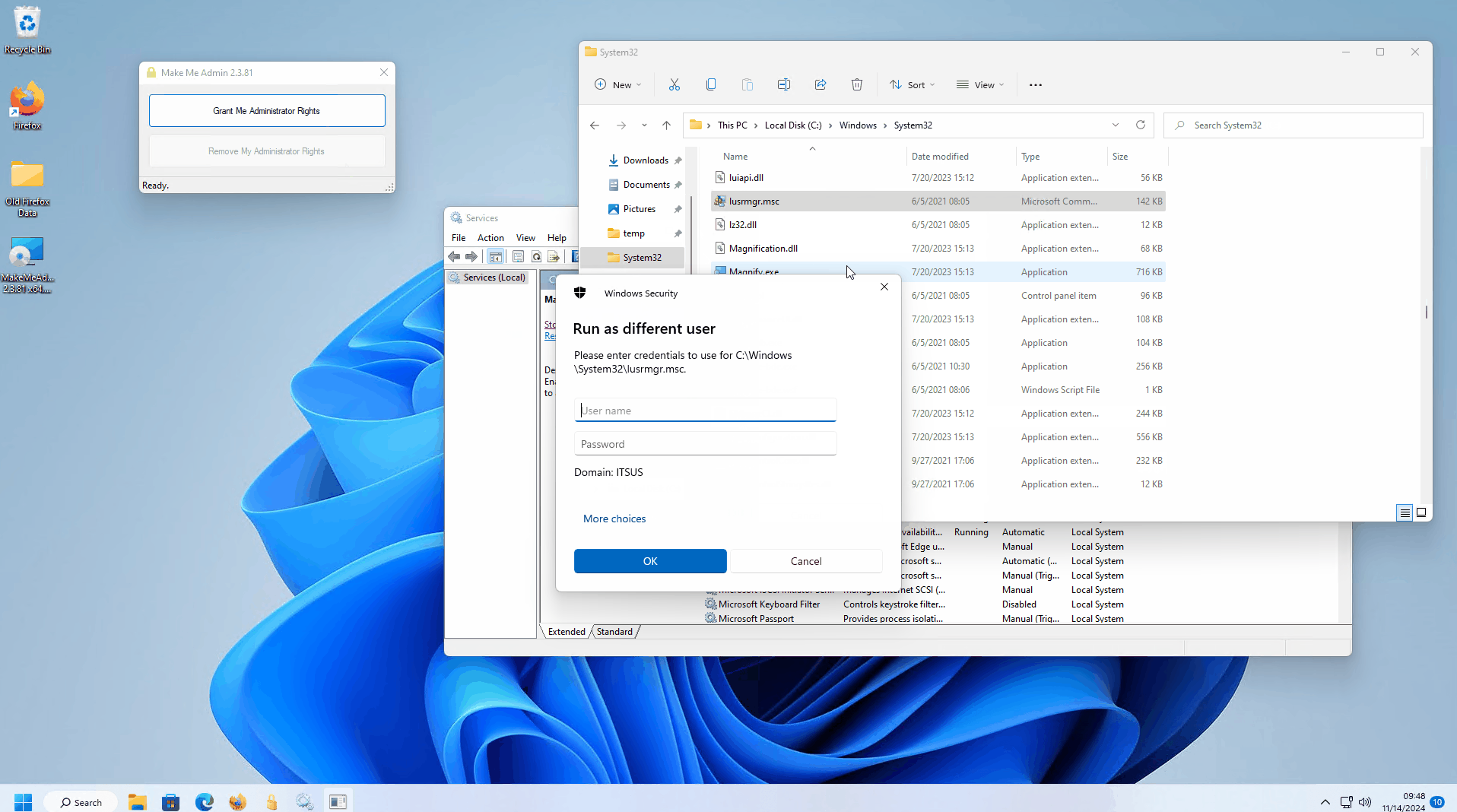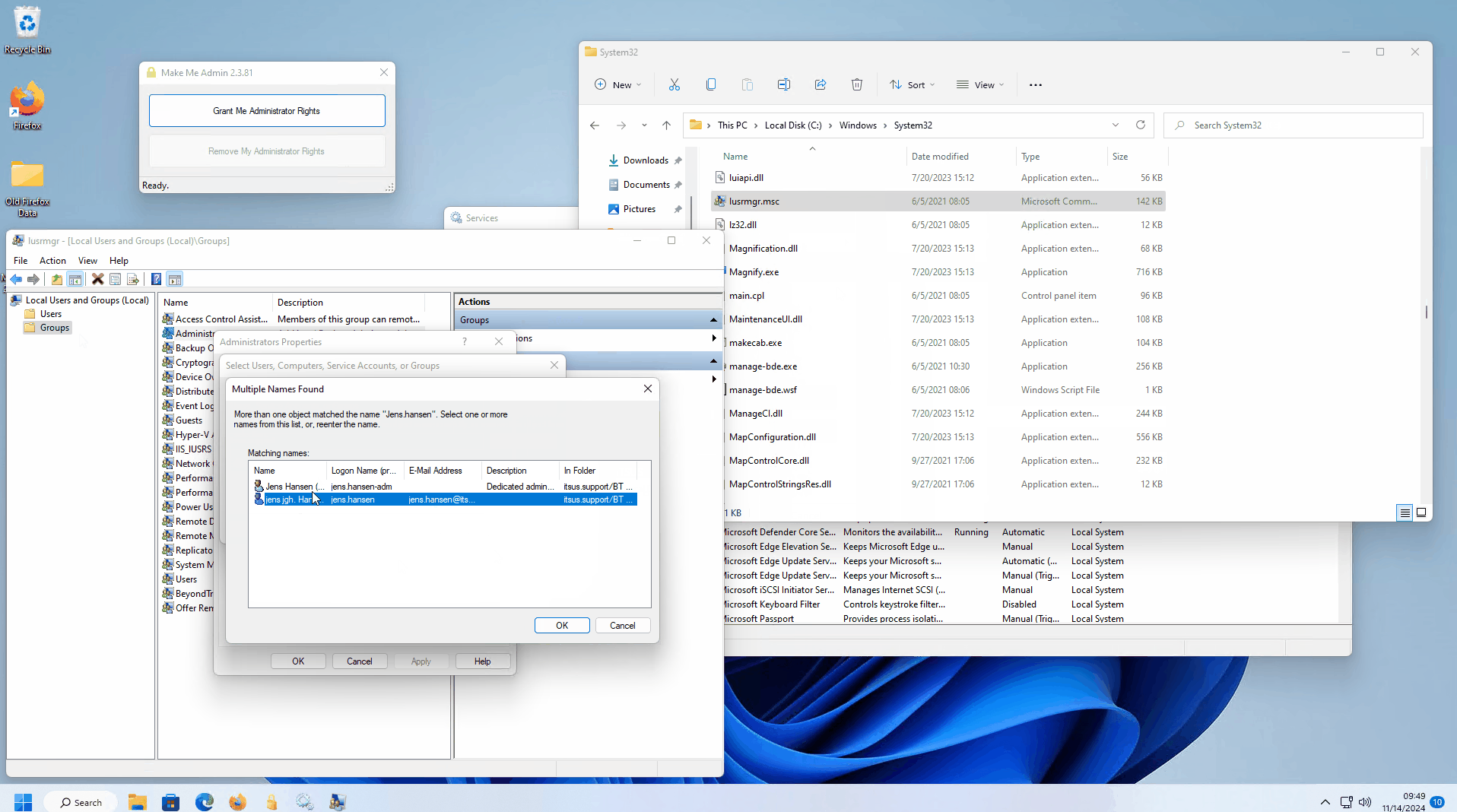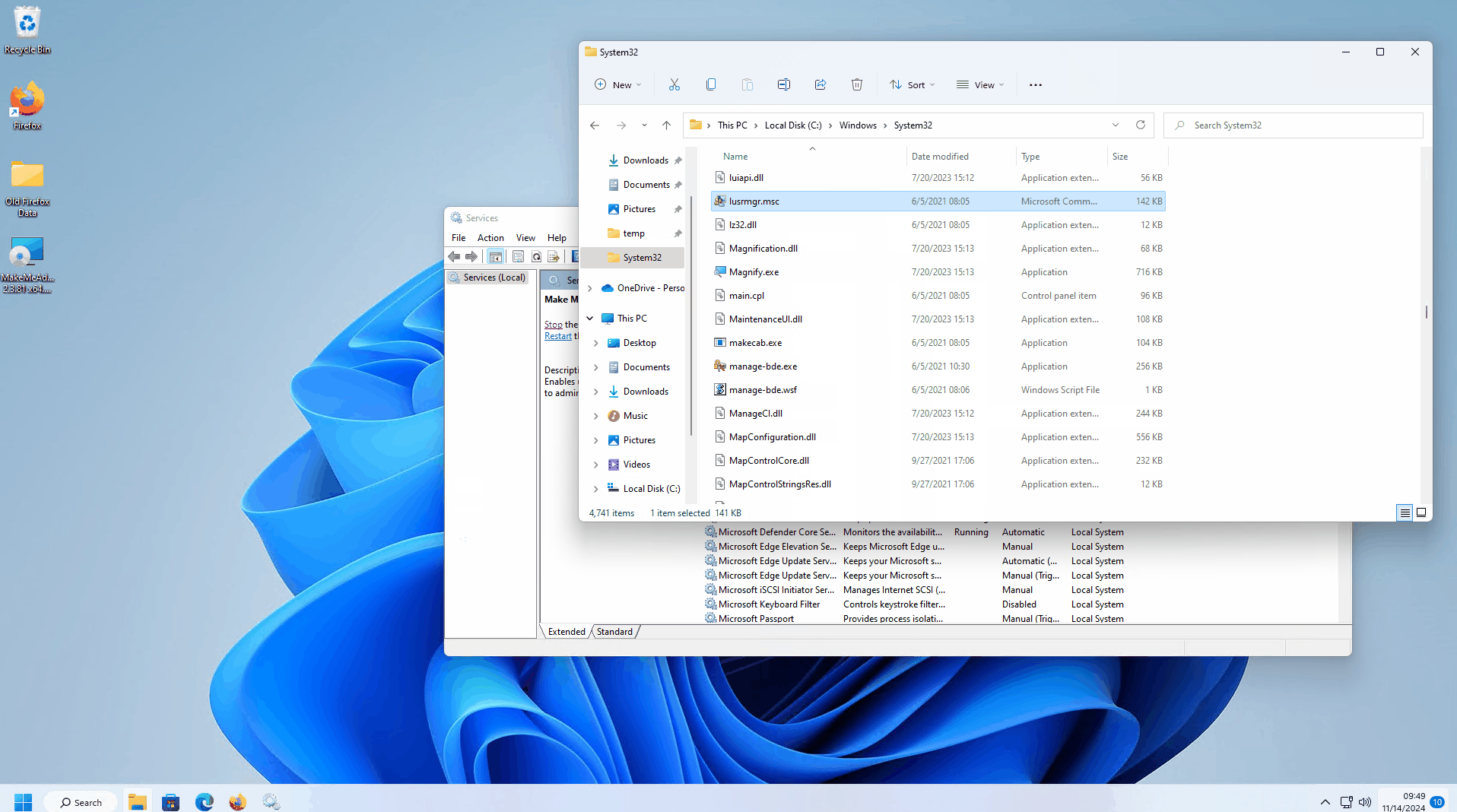
Hi , while doing some testing it looks like end users can easily bypass EPM agent at least on windows by using other privilege delegation tools such as Make Me Admin (which is available on Github). If it is not blocked , a user can simply become a temporary admin using Make Me Admin and then stop the avecto service to bypass EPM protections.
is there a way EPM can monitor and block addition of users to local administrator group ? (This is the method used by Make Me Admin tool) .
Question
EPM Windows - tools/apps to be blocked in order to avoid bypassing EPM
Reply
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.