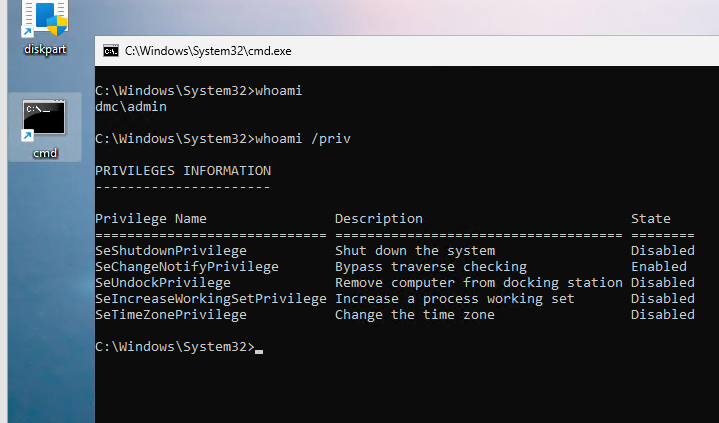
We’re running EPM in a mostly windows environment. Some support/admin users have secondary accounts that have all their elevated AD credentials, like domain admin for example. When we try to run an elevated command prompt it opens it as admin of the current/primary user account. They need to be able to open an admin CMD as the second user that has the elevated AD credentials.
Any suggestions on how to pull that off? The users are all in a high flex workstyle.
Thanks.