I’m trying to figure out if this is even possible. I feel like it is, but I’m probably missing how to accomplish it.
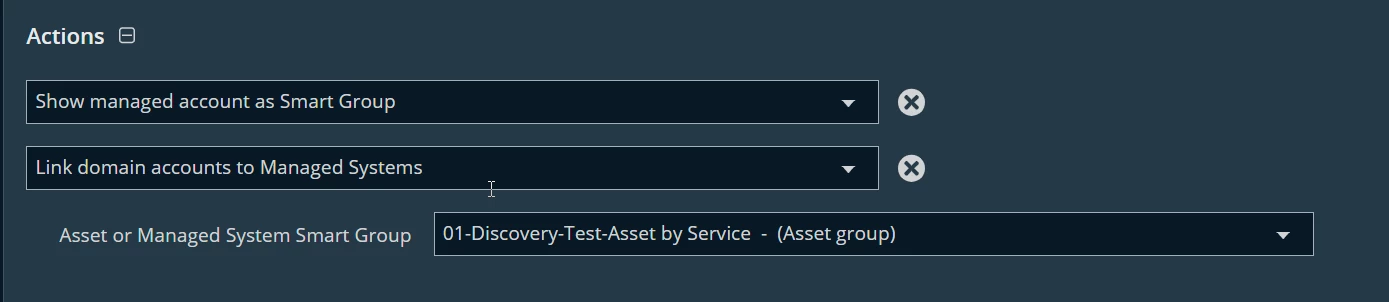
So we have 60 something Windows servers running SQL server. We have 20 something AD accounts that run SQL on these various servers. Ideally what I’d like to do is build a rule that adds the appropriate linked managed system to each managed account that is running the SQL services on those systems. So the end result would be I could go into each account, and see the system or systems that it is running SQL on.
I’d really like this to work automatically so that any time a new server is added, or an account is added to another system, it automatically gets added to the list of linked systems for that account. I can easily create rules to get a list of all of these servers running sql. I can also easily create a rule that shows me all of these accounts (they all start with the same thing). But is there a way to then just link each account to the appropriate server without creating tons of different rules?