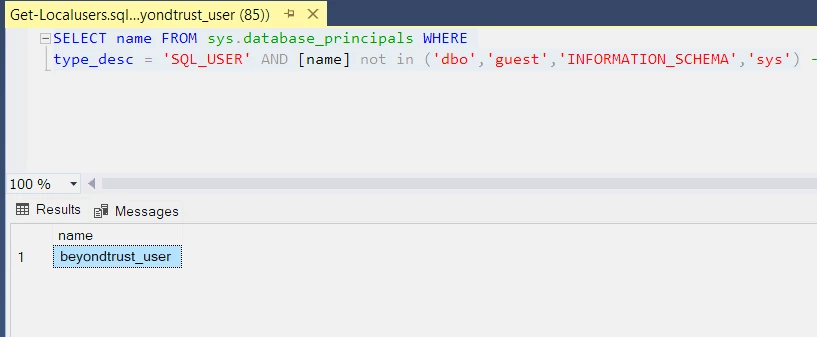
trying to scan SQL server databases getting all the databases but no local accounts any help will be greatly appreciated
Question
can you scan for local sql sevrer accounts
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.