Hi All
I am facing one issue in mapping dedicated account for ids on local dmz servers. admin id and users standard ids are not matching. in such case how should use the dedicated account mapping functionality?
Below is data set-up
1. admin id on managed system is PAO12345
2. standard id of this user in user group is MSS12345
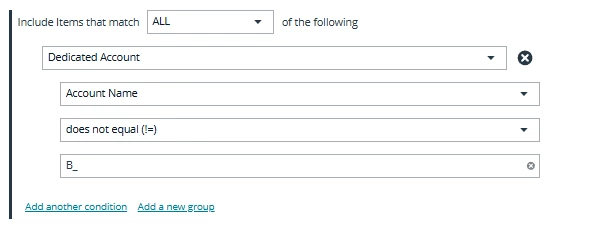
Now since admin id is local i cannot use directory attribute. in mapping Smart rule i think we cannot use map dedicated account to action with deciated account filter.
Kindly help me how can i write the smart rule to map the deciated ids . I don't want to use one-to-one mapping as it will require to write lot of smart rule and lot of user group.
Please help