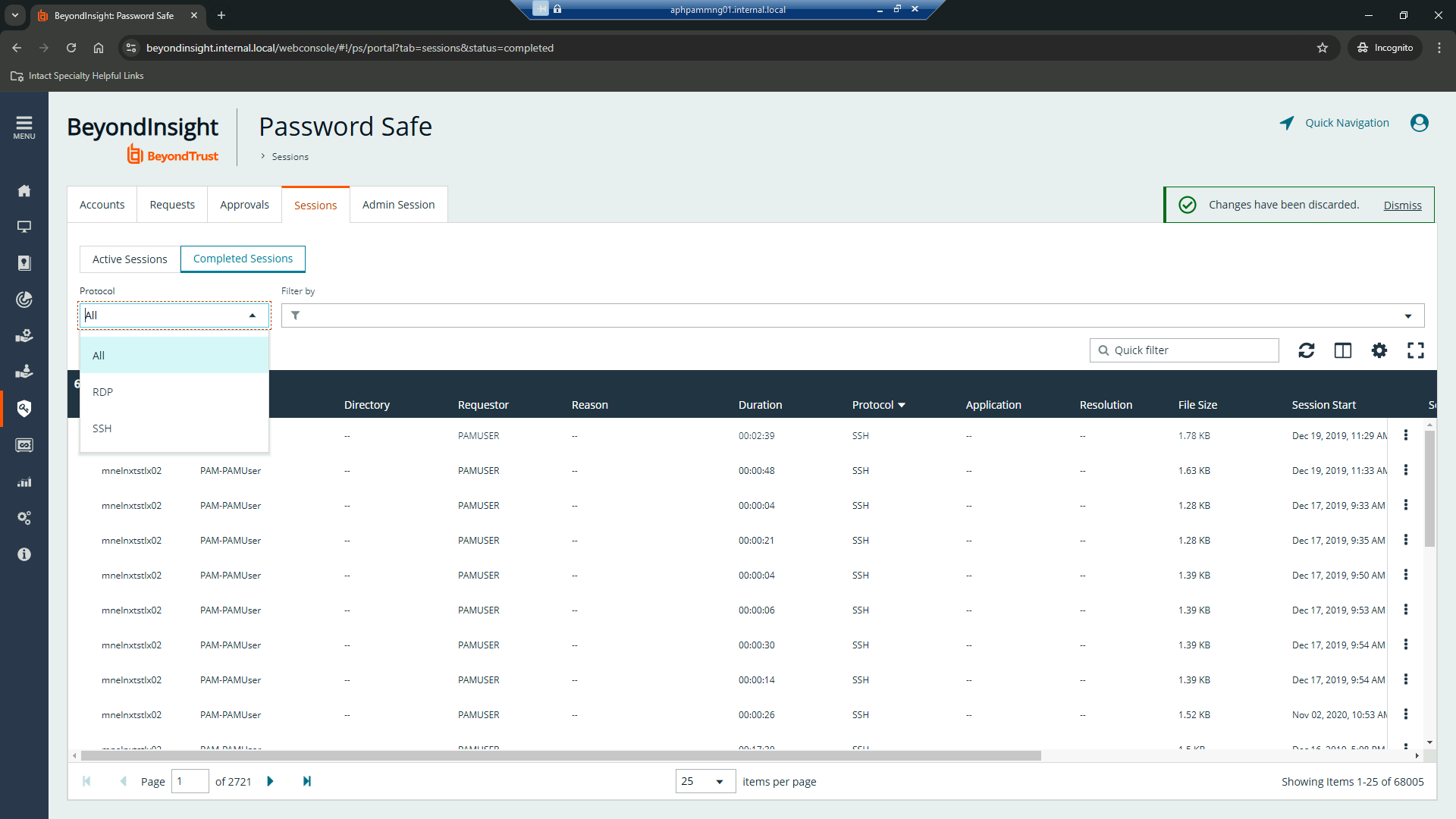
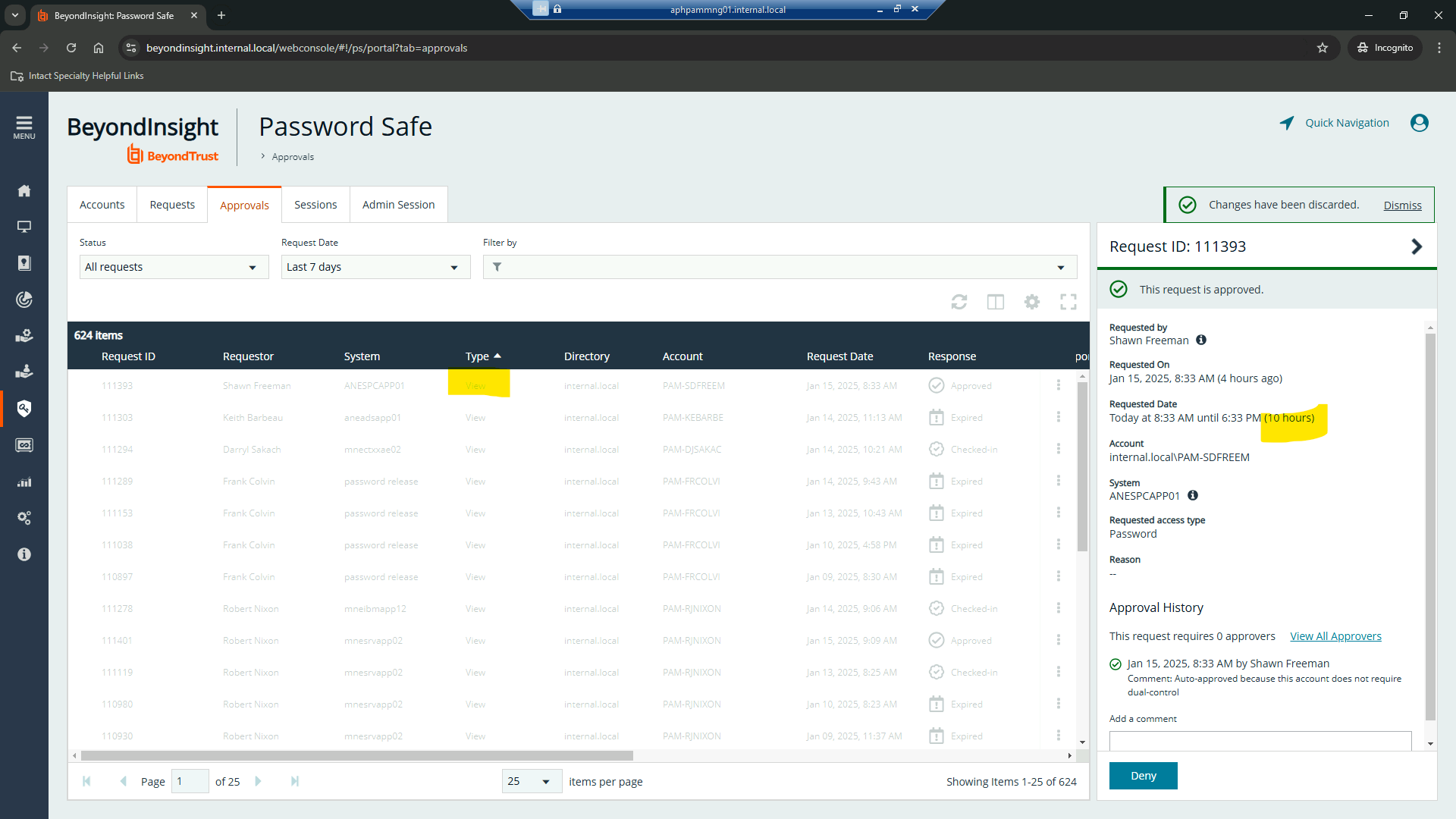
We have several issues, and resolving them would be very easy if we can get information from the users session request, specifically duration. we have turned off ESA and log off on disconnect due to business use requirements so if a user does not sign out of an RDO session properly the privileged account will become locked after password safe does a post release password reset. in the most recent case the user is getting locked out and we find this through a daily lockout report from our SEIM. the user is notified and claps back that she has not been on the machine in days. in researching we see she accessed this sever and failed to logout properly 7 days earlier. we assume the user requested this session for 7 days, however the user does not remember. we would like to address this but with no solid evidence we cannot do that. any suggestions?
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.