I keep getting duplicate devices in the console, how do you prevent these from running up your license count? Is there a tool we can use to find the duplicated devices or is it just hunt and peck through thousands of devices?
Easy way to find and remove duplicate clients in Admin console.
Best answer by mjhall
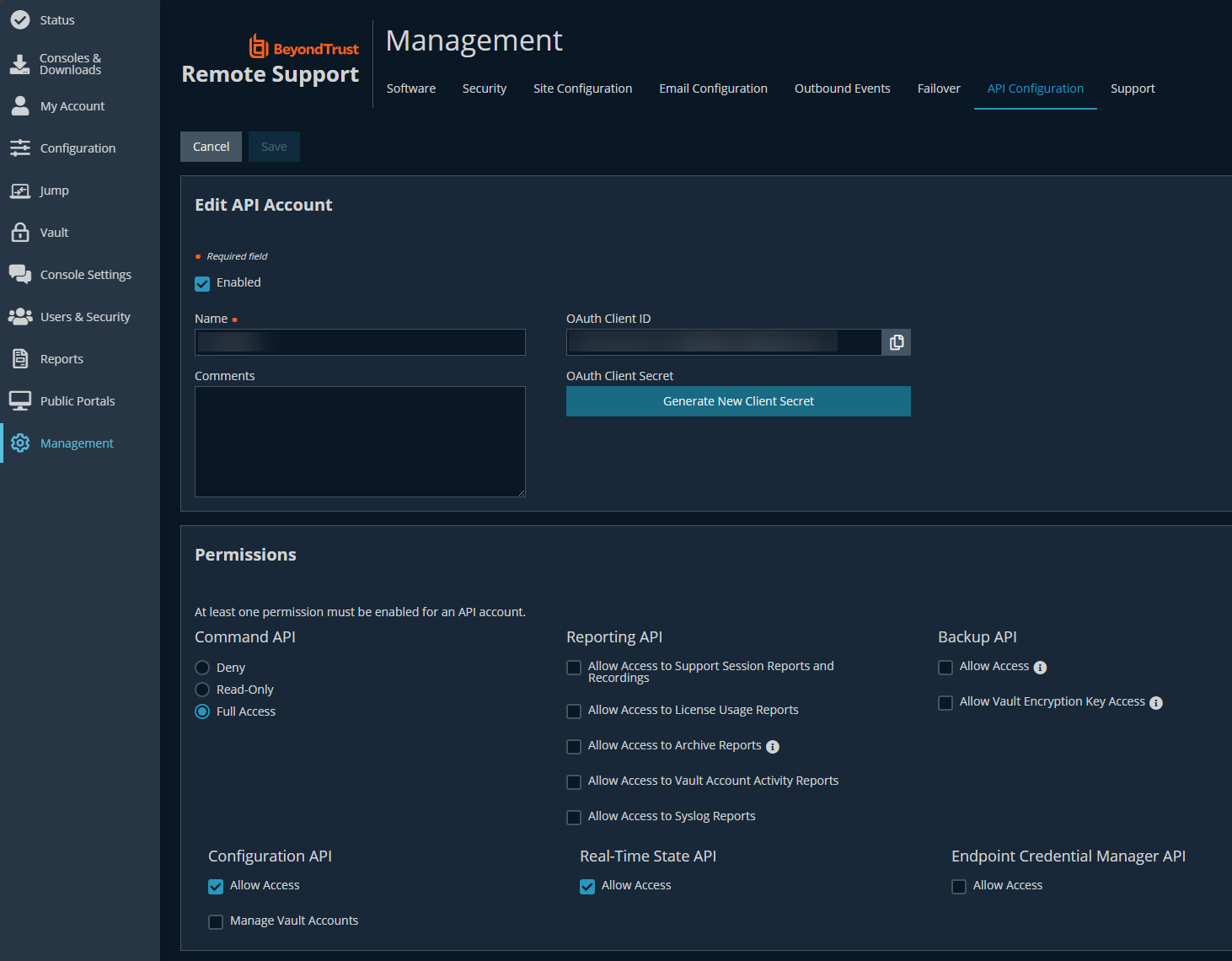
This is all very well documented as well so I’d point you that direction, but you’ll need to create an API account in /login which I believe needs these three access policies (that’s what my account has anyways) -
- Command API: Full Access
- Configuration API
- Real-Time State API
This is where you also get the secret and client ID for using the API. It must not be against community policy to share code since they have a little code button. Hopefully you are familiar with PowerShell. This is a stripped down, non-tested version of what I’m doing. I took out logging, error handling, and other out of scope to this conversation code to try fitting it in this post better. If others are seeing this and have feedback, I’m open to hear it, but I am not open to the “*scoff* Why are you doing it that way” comments 😂 It has been working great in my environment, and we get a few dozen duplicates a month roughly with workstation reloads and what not.
<#
Author:
Date:
This script is used to manage Jump Clients in the BeyondTrust Remote Support environment.
It removes duplicate clients and logs all actions to a file.
The script takes three mandatory parameters: Secret, ClientID, and Namespace.
Secret and ClientID are used for API authentication, and Namespace is used to specify the API endpoint.
To run this script, use the following command in PowerShell:
.\YourScript.ps1 -Secret "YourSecret" -ClientID "YourClientID" -Namespace "YourNamespace"
Replace YourScript.ps1 with the name of this script file, and replace YourSecret, YourClientID, and YourNamespace with your actual values.
#>
param (
[Parameter(Mandatory=$true)]
[string]$Secret,
[Parameter(Mandatory=$true)]
[string]$ClientID,
[Parameter(Mandatory=$true)]
[string]$Namespace
)
# Authorization region
$EncodeCred = [Convert]::ToBase64String([System.Text.Encoding]::utf8.GetBytes($ClientID + ":" +$Secret))
# Get auth token
$AuthToken = Invoke-RestMethod -Method POST -Header @{"authorization" = "Basic $EncodeCred"} -body @{"grant_type"="client_credentials"} -uri "https://$Namespace/oauth2/token"
$Token = $AuthToken.access_token
# Initialize unique clients hashtable for removing duplicates
$UniqueClients = @{}
# Initialize page index and max page
$PageIndex = 1
$PageMax = 50 # Prevents corner case of having exactly x00 clients and loops forever
# Loop through the pages of data from the API
do{
# Query the API to get 100 records
$JumpClientList = Invoke-RestMethod -Method Get -Headers @{"authorization"="Bearer $Token"; "Accept"="application/json"} -Uri "https://$Namespace/api/config/v1/jump-client?current_page=$PageIndex"
# Loop through each record
foreach($JumpClient in $JumpClientList){
# Remove duplicates logic
if ($UniqueClients.ContainsKey($JumpClient.hostname)) {
# Update the hashtable if the current timestamp is more recent
if ($UniqueClients[$JumpClient.hostname].id -ne $JumpClient.id -AND [datetime]$JumpClient.last_connect_timestamp -gt [datetime]$UniqueClients[$JumpClient.hostname].last_connect_timestamp) {
# Get the bad ID
$IDToRemove = $UniqueClients[$JumpClient.hostname].id
# Remove the jump client with an API call
Invoke-RestMethod -Method Delete -Headers @{"authorization"="Bearer $Token"} -Uri "https://$Namespace/api/config/v1/jump-client/$IDToRemove" | Out-Null
# Replace the jump client in the hashtable
$UniqueClients[$JumpClient.hostname] = $JumpClient
} elseif($UniqueClients[$JumpClient.hostname].id -ne $JumpClient.id -AND [datetime]$JumpClient.last_connect_timestamp -lt [datetime]$UniqueClients[$JumpClient.hostname].last_connect_timestamp){
# Remove the current one we are looking at
# Get the bad ID
$IDToRemove = $JumpClient.id
# Remove the jump client with an API call
Invoke-RestMethod -Method Delete -Headers @{"authorization"="Bearer $Token"} -Uri "https://$Namespace/api/config/v1/jump-client/$IDToRemove" | Out-Null
}
} else {
# Add the item to the hashtable if the hostname is not present
$UniqueClients[$JumpClient.hostname] = $JumpClient
}
## You can do other things down here with the jump client records now that you are building the list. In my environment I set the comments field with various info.
}
# Increment the page index
$PageIndex++
} while($JumpClientList.count -eq 100 -and ($PageMax - $PageIndex) -gt 0)
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.