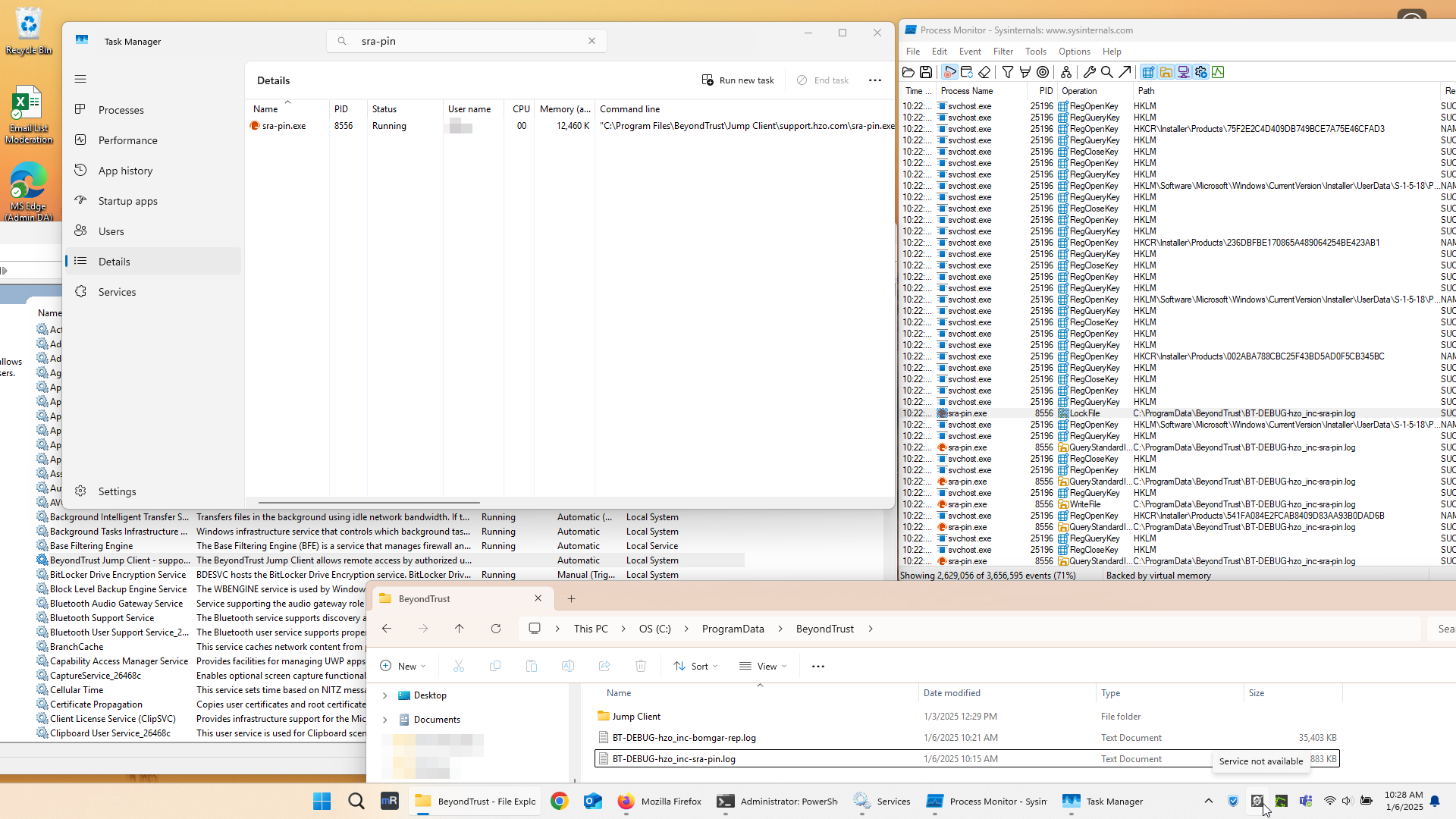
Here is my list of problems:
- The new agent running as sra-pin.exe has been deployed as of v24.3.1 but the old bomgar-scc.exe and remnants are still installed on upgraded systems, including the service.
- The new agent upgrade removed the ability of the old agent to be removed from Add/Remove programs, requiring manual registry scrubbing and file deletion.
- The new agent installs on diffierent locations depending if it’s upgraded or newly installed, making it almost impossible to detect via automation tools like InTune.
- The old process bomgar-scc.exe is still used when agent connects to a jump client, even though this process does not exist anywhere as executable before the connection is made.
- The new agent service stops running and does not resume, even after reboots. However, the sra-pin.exe process can be found running under the user context. The device shows offline regardless.
- Reinstalling the agent does not resolve this log term, after a day or so the agent goes back offline.
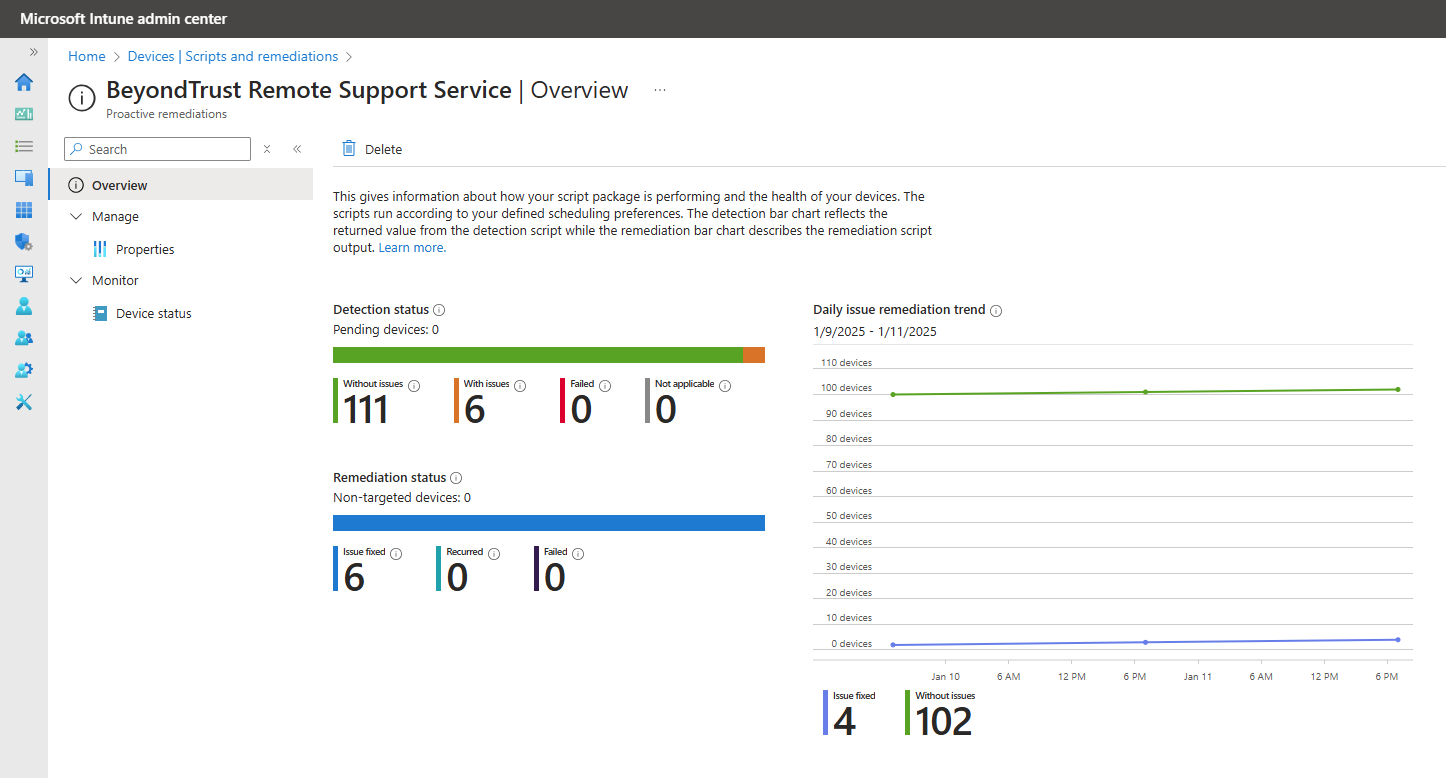
- Most devices are now showing offline, and some are in locations where IT support is not available, creating a very difficult situation.
- Complete uninstall and reinstall is not possible because of our company global span and many jump groups.
- Opened case has gone nowhere, the rep is offering a downgrade to 24.2.4 or waiting on the new release, without addressing how the offline agents will be handled.
Here is a screenshot I sent recently to support that covers most of the problems listed below.