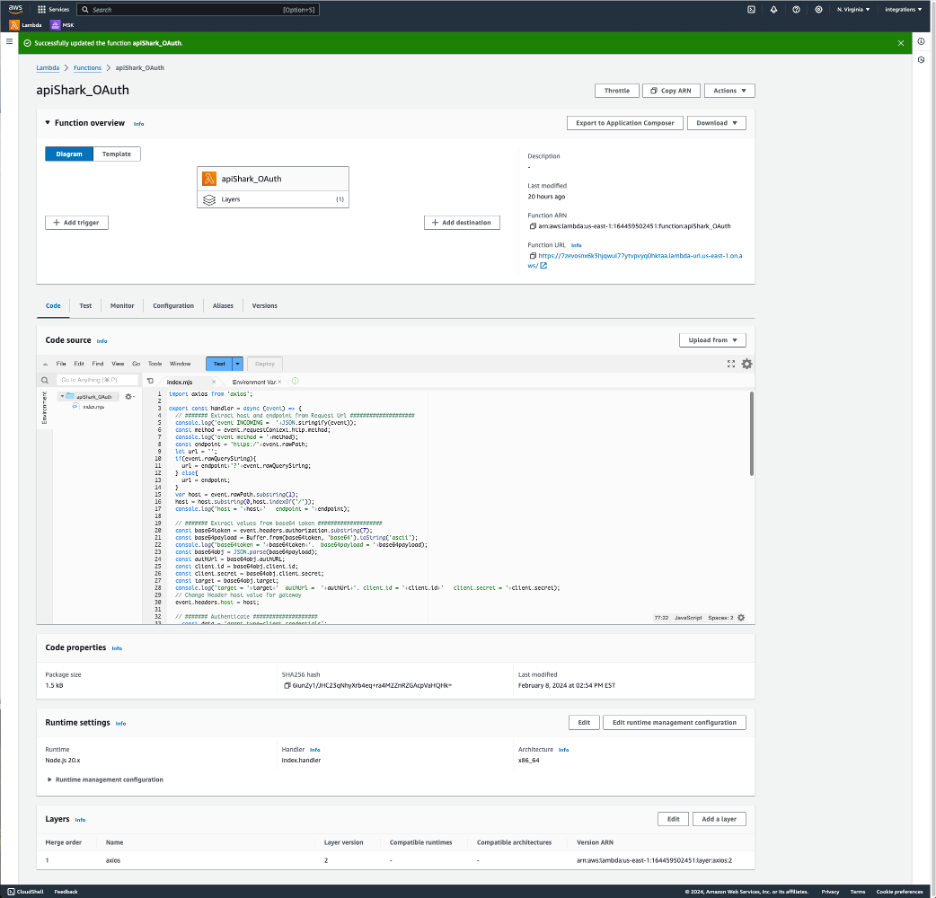
Why introducing AWS Lambda function
The main reason the integration is leveraging a Lamdba function is to overcome the lack of support in Okta for OAuth client credentials.
Source:
https://developer.okta.com/docs/concepts/scim/faqs/
Disclaimer
Any sample or proof of concept code (“Code”) provided on the Community is provided “as is” and without any express or implied warranties. This means that we do not promise that it will work for your specific needs or that it is error-free. Such Code is community supported and not supported directly by BeyondTrust, and it is not intended to be used in a production environment. BeyondTrust and its contributors are not liable for any damage you or others might experience from using the Code, including but not limited to, loss of data, loss of profits, or any interruptions to your business, no matter what the cause is, even if advised of the possibility of such damage.
Q: How should I be managing authentication to my SCIM API?
Okta recommends using the OAuth 2.0 Authorization Code grant flow. Okta doesn't support the Client Credentials or Resource Owner Password Credentials Authorization grant flows for SCIM. The Authorization Code grant flow is more common in SaaS and cloud integrations and is also more secure.
Comment: Okta is stating that Authorization Code grant flow is more secure, but it means that when Okta SCIM App needs to authenticate to Password Safe, it would actually be Password Safe that would have to authenticate back to Okta, using Client ID and Client Secret generated by Okta. This translate into PAM trusting the Directory, when it should be the other around, from a Security Best Practices point of view.
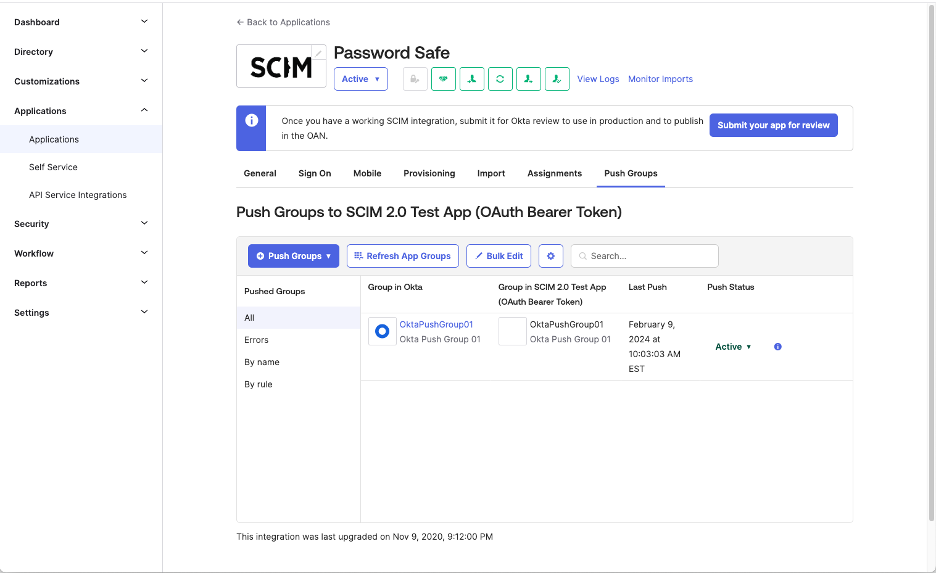
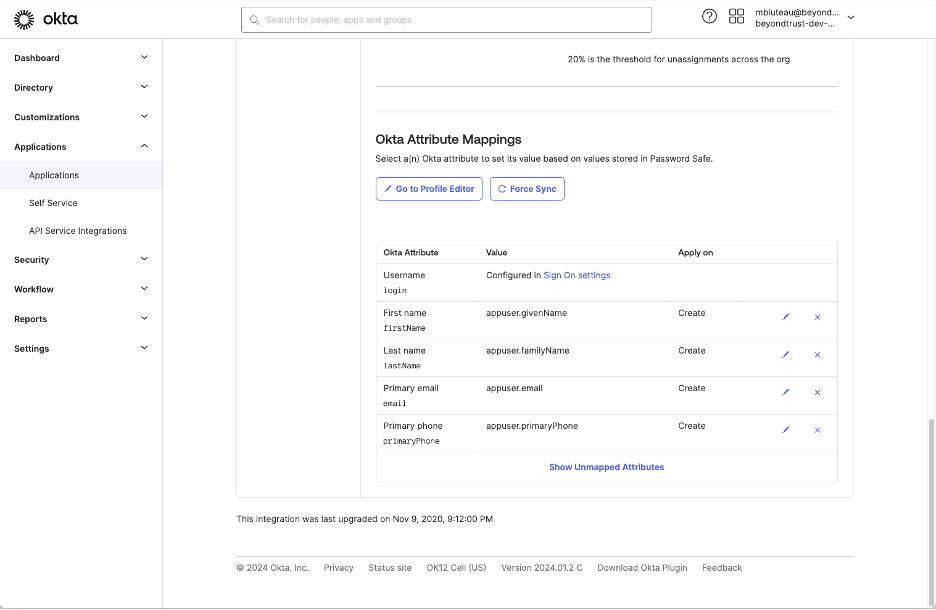
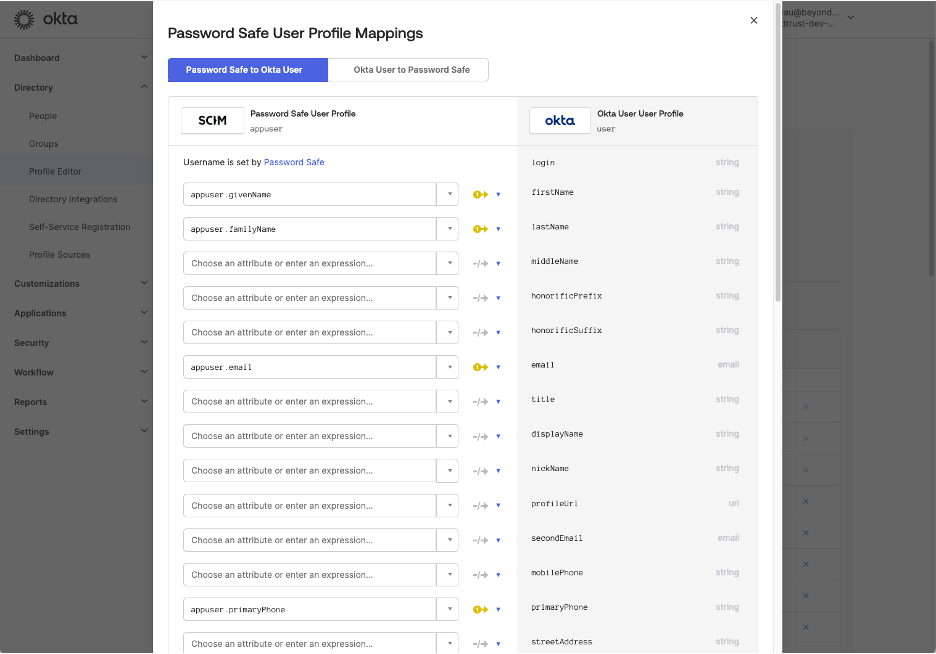
Another reason is to enable the support for Okta Group Push. Password Safe requires a description attribute at creation time, and Okta only provides a displayName attribute, which makes the Okta Push provisioning request to fail, being an invalid request missing the mandatory attribute description.
AWS Lambda function
Prerequisites and configuration
- AWS instance or AWS free tier: https://aws.amazon.com/free
- Nodejs axios layer: https://docs.aws.amazon.com/lambda/latest/dg/chapter-layers.html
- Function code:
import axios from 'axios';
// Set logLevel to debug to enable debug logs. WARNING: Credentials and Access Token are exposed with debug.
const logLevel = "debug";
export const handler = async (event) => {
// Extract host and endpoint from Request Url
if(logLevel == "debug"){console.log('event INCOMING = '+JSON.stringify(event));}
const method = event.requestContext.http.method;
console.log('event method = '+method);
const endpoint = 'https:/'+event.rawPath;
let url = '';
if(event.rawQueryString){
url = endpoint+'?'+event.rawQueryString;
} else{
url = endpoint;
}
var host = event.rawPath.substring(1);
host = host.substring(0,host.indexOf('/'));
console.log('host = '+host+' endpoint = '+endpoint);
// Extract values from base64 token
const base64token = event.headers.authorization.substring(7);
const base64payload = Buffer.from(base64token, 'base64').toString('ascii');
if(logLevel == "debug"){console.log('base64token = '+base64token+'. base64payload = '+base64payload);}
const base64obj = JSON.parse(base64payload);
const authUrl = base64obj.authURL;
const client_id = base64obj.client_id;
const client_secret = base64obj.client_secret;
const target = base64obj.target;
console.log('target = '+target+' authUrl = '+authUrl);
// Change Header host value for gateway
event.headers.host = host;
// Authenticate
var access_token = '';
try{
//const data = 'grant_type=client_credentials';
const data = 'grant_type=client_credentials&client_id=' + client_id + '&client_secret=' + client_secret;
//const authorization = 'Basic ' + Buffer.from(client_id+':'+client_secret).toString('base64');
const authConfig = {
method: 'post',
rejectUnauthorized: false,
url: authUrl,
data: data,
headers: {
'Content-Type': 'application/x-www-form-urlencoded',
// 'Content-Type': 'application/json',
'Content-Length': data.length,
// 'Authorization': authorization,
'Host': host,
'Accept': '*/*'
}
};
if(logLevel == "debug"){console.log('authConfig = '+JSON.stringify(authConfig));}
const authRes = await axios(authConfig);
if(logLevel == "debug"){console.log('authRes = '+ authRes);}
if(logLevel == "debug"){console.log('authRes JSON.stringify = '+JSON.stringify(authRes.data));}
access_token = authRes.data.access_token;
}
catch(err){
console.log('auth error = ' + err);
//console.log('auth error response = ' + err.response);
}
// GET, POST, PATCH data
if(target == "PasswordSafe" && endpoint == 'https://'+host+'/scim/v2/Groups' && method == 'POST'){
console.log('We have a Password Safe Create Group call body : '+JSON.stringify(event.body));
const body = JSON.parse(event.body);
console.log('PUSH Group body = '+JSON.stringify(body));
const data = {
"schemas": [
"urn:ietf:params:scim:schemas:core:2.0:Group"
],
"displayName": body.displayName,
"description": body.displayName,
"members": body.members
};
const configG = {
method: method,
url: url,
headers: {
'Content-Type': event.headers['content-type'],
'Content-Length': data.length,
'Accept': event.headers.accept,
'Authorization': 'Bearer '+access_token,
'Host': host
},
"data": data
};
if(logLevel == "debug"){console.log('Password Safe Create Group: configG = '+JSON.stringify(configG));}
try{
const resG = await axios(configG);
// Response - For testing only
resG.headers['content-type'] = 'application/scim+json';
console.log('axios res data = '+JSON.stringify(resG.data));
console.log('axios res headers = '+JSON.stringify(resG.headers));
const response = {
statusCode: resG.status,
body: JSON.stringify(resG.data),
headers: resG.headers
};
return response;
}
catch (err) {
console.log('Password Safe Create Group: error = '+JSON.stringify(err));
}
}
else {
var config = {};
if(event.body){
config = {
method: method,
url: url,
headers: {
'content-type': event.headers['content-type'],
'content-length': event.headers['content-length'],
'accept': event.headers.accept,
'Authorization': 'Bearer '+access_token,
'host': host
},
data : event.body
};
} else {
config = {
method: method,
url: url,
headers: {
'Accept': 'application/json',
'Authorization': 'Bearer '+access_token,
'host': host
}
};
}
if(logLevel == "debug"){console.log('axios config = '+JSON.stringify(config));}
try{
const res = await axios(config);
// Response - For testing only
res.headers['content-type'] = 'application/scim+json';
console.log('axios res data = '+JSON.stringify(res.data));
console.log('axios res headers = '+JSON.stringify(res.headers));
const response = {
statusCode: res.status,
body: JSON.stringify(res.data),
headers: res.headers
};
return response;
}
catch (err) {
console.log('error = '+JSON.stringify(err));
}
}
};

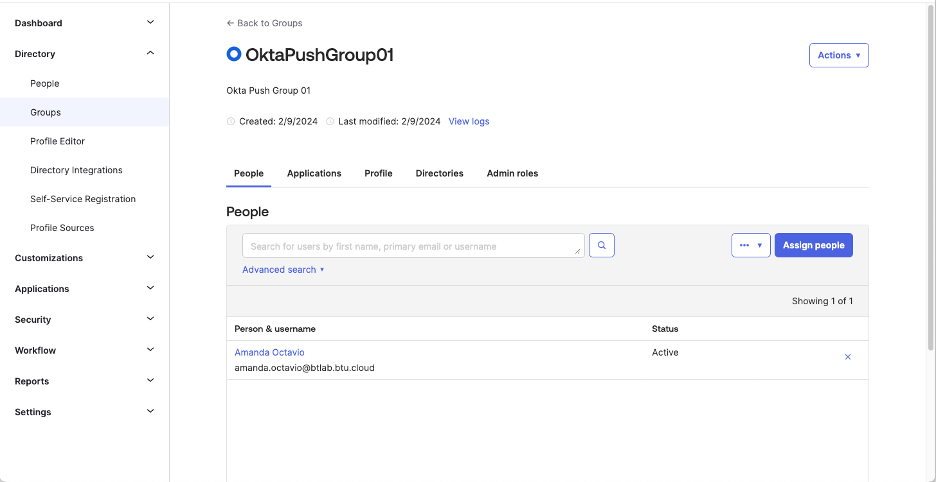
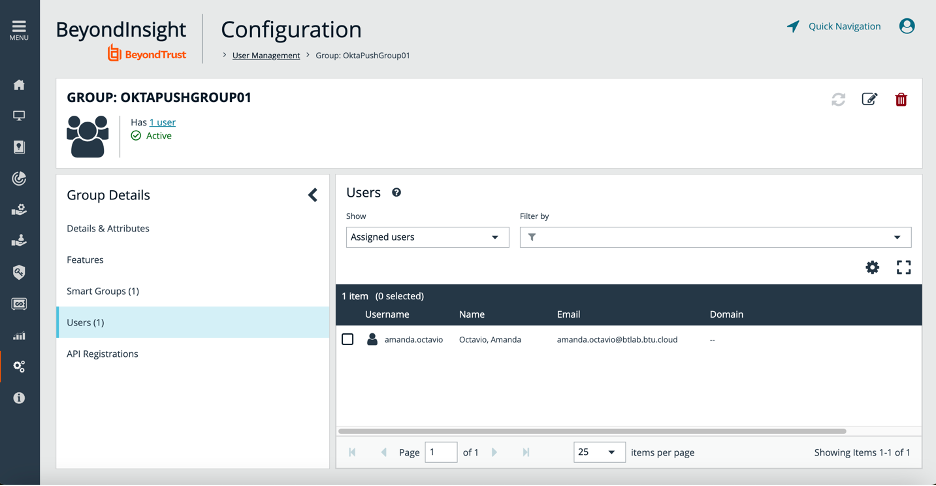
Before configuration Okta SCIM App
SCIM 2.0 Base Url and OAuth Bearer Token
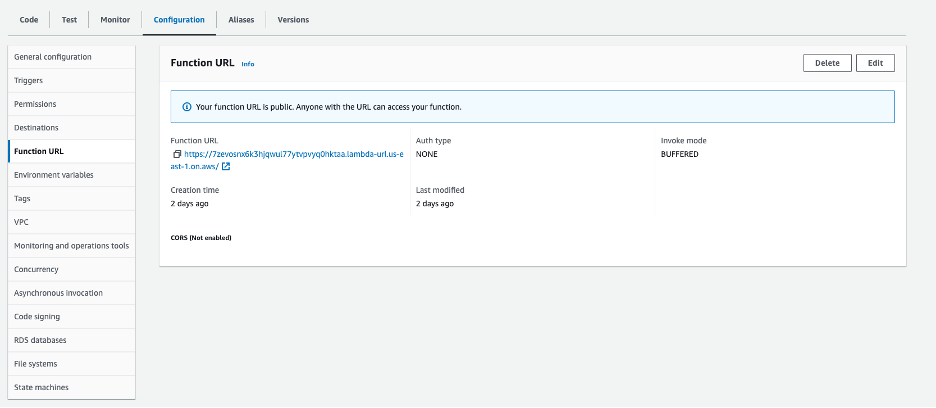
The SCIM 2.0 Base Url is the Function URL with the Password Safe Url (minus https://) appended to it, for example:
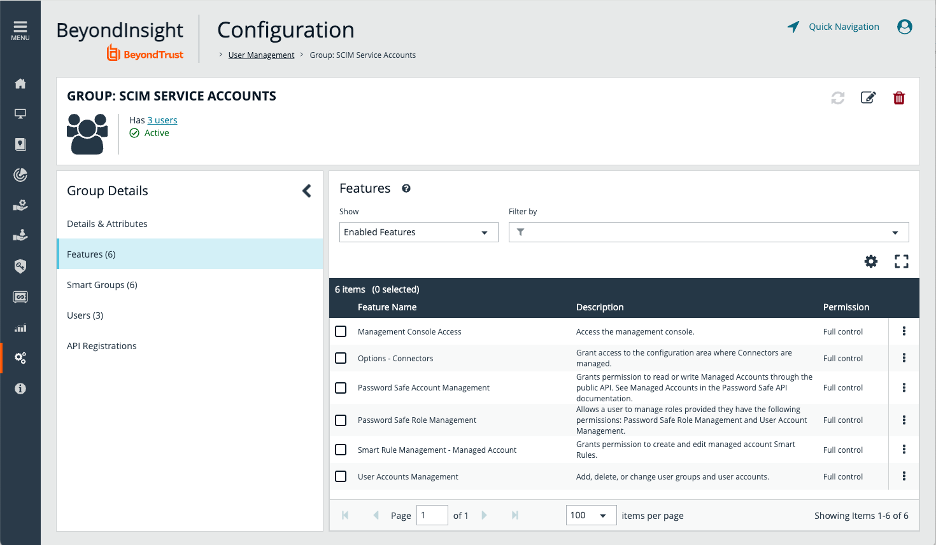
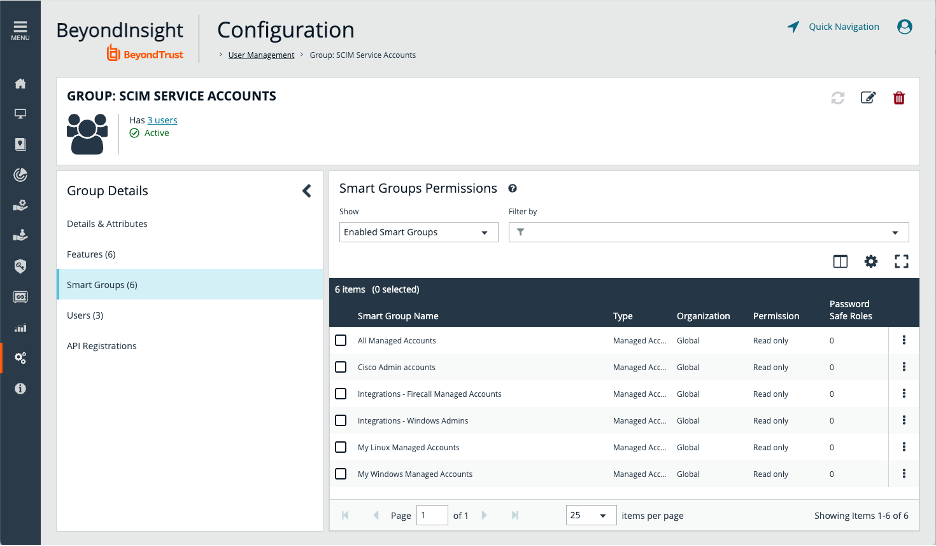
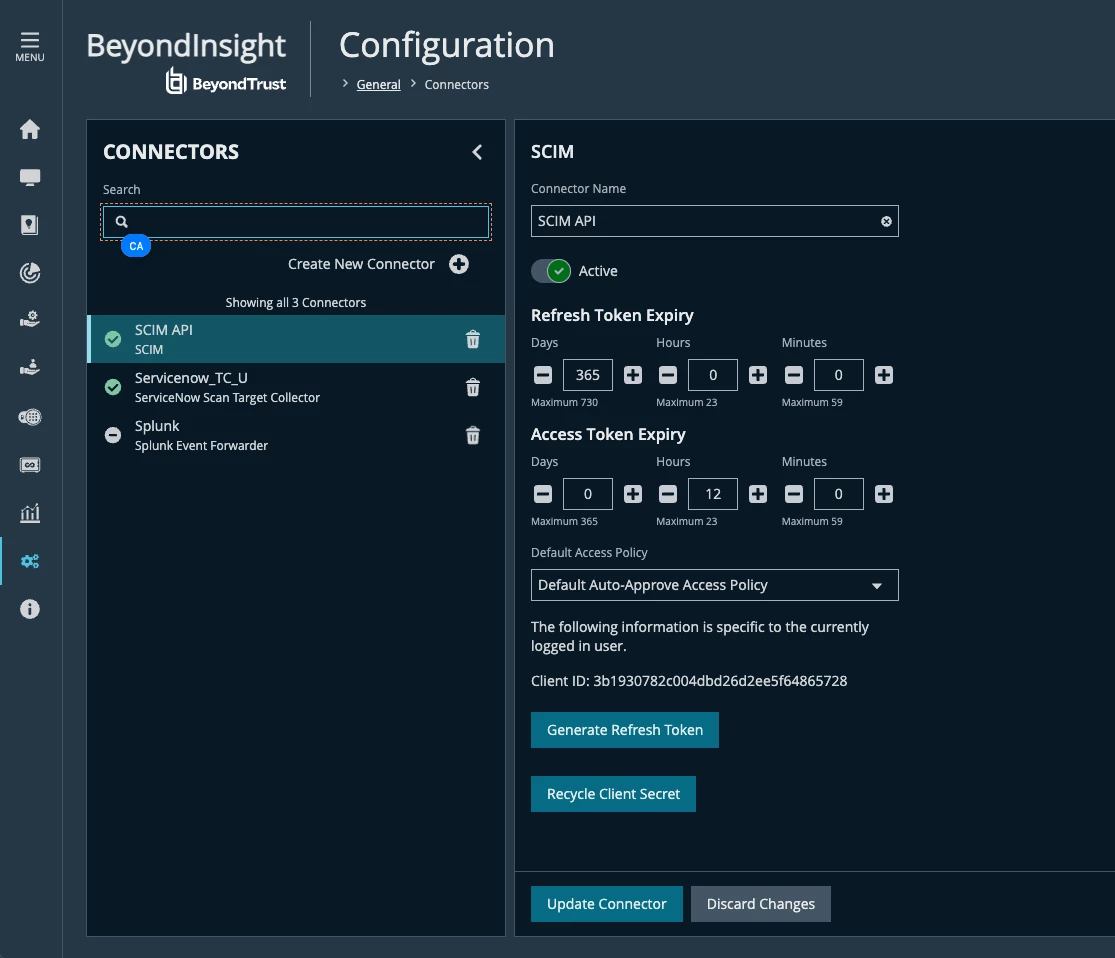
Note: A Single SCIM Connector can be created for a Password Safe instance. Each user that has access to the SCIM Connector can generate his or her own Client ID and Secret. DO NOT USE ADMINISTRATOR to generate the Client ID and Secret.
To create the Bearer Token for Okta, we must first create a JSON document:
{"target":"PasswordSafe","authURL":"https://pws_instance.ps.beyondtrustcloud.com/scim/oauth/token","client_id":"b0d00123456abcde4a7611b9","client_secret":"63eee16d6b3456789012vfdes1bc5e6"}
Then we need to create a base64 encoded version, e.g. by using https://base64encode.org :
eyJ0YXJnZXQiOiJQYXNzd29yZFNhZmUiLCJhdXRoVVJMIjoiaHR0cHM6Ly9wd3NfaW5zdGFuY2UucHMuYmV5b25kdHJ1c3RjbG91ZC5jb20vc2NpbS9vYXV0aC90b2tlbiIsImNsaWVudF9pZCI6ImIwZDAwMTIzNDU2YWJjZGU0YTc2MTFiOSIsImNsaWVudF9zZWNyZXQiOiI2M2VlZTE2ZDZiMzQ1Njc4OTAxMnZmZGVzMWJjNWU2In0=
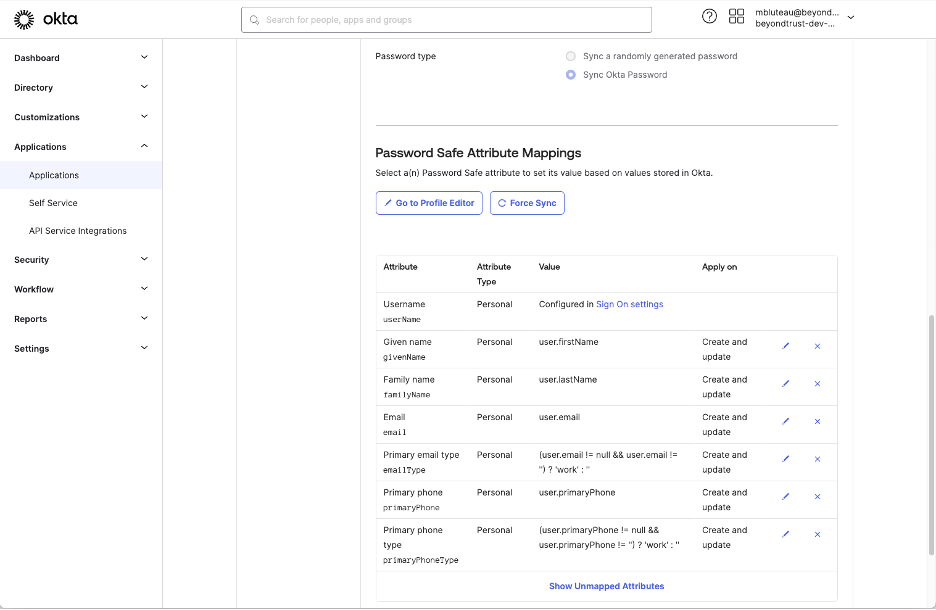
Configure Okta SCIM App
SCIM 2.0 Base Url and OAuth Bearer Token
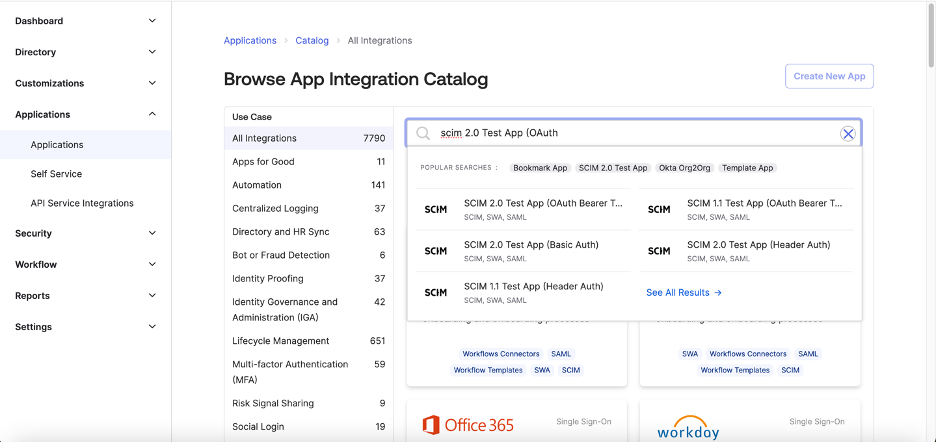
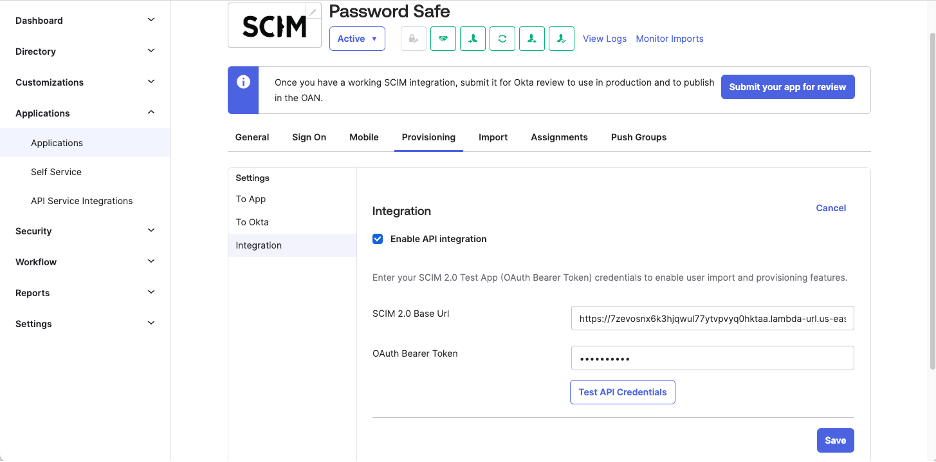
Url format is: {AWS Lambda Function URL}/my_instance.ps.beyondtrustcloud.com/scim/v2
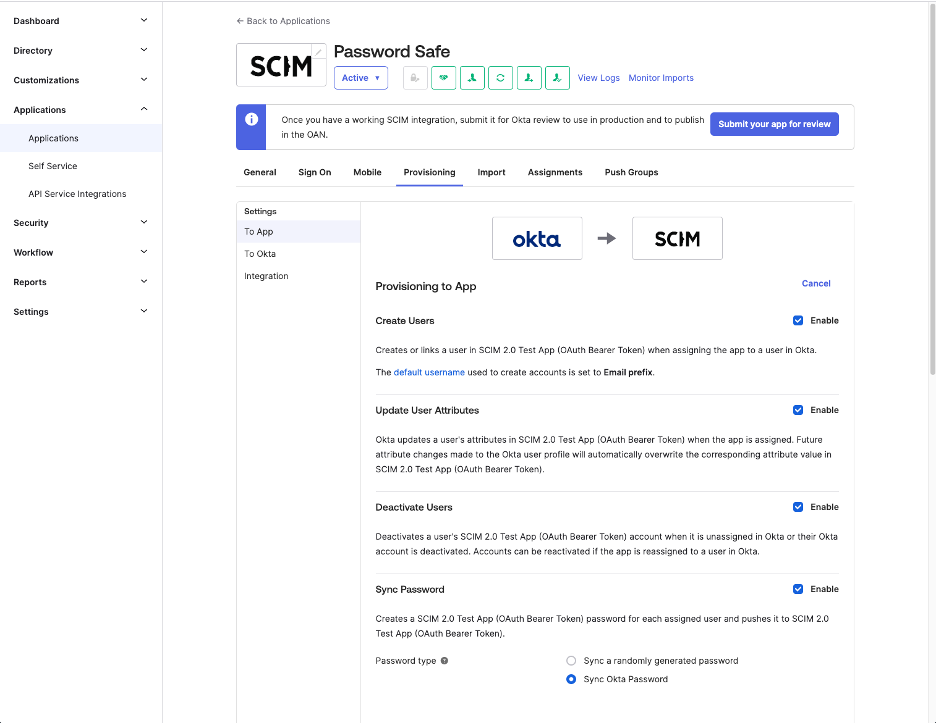
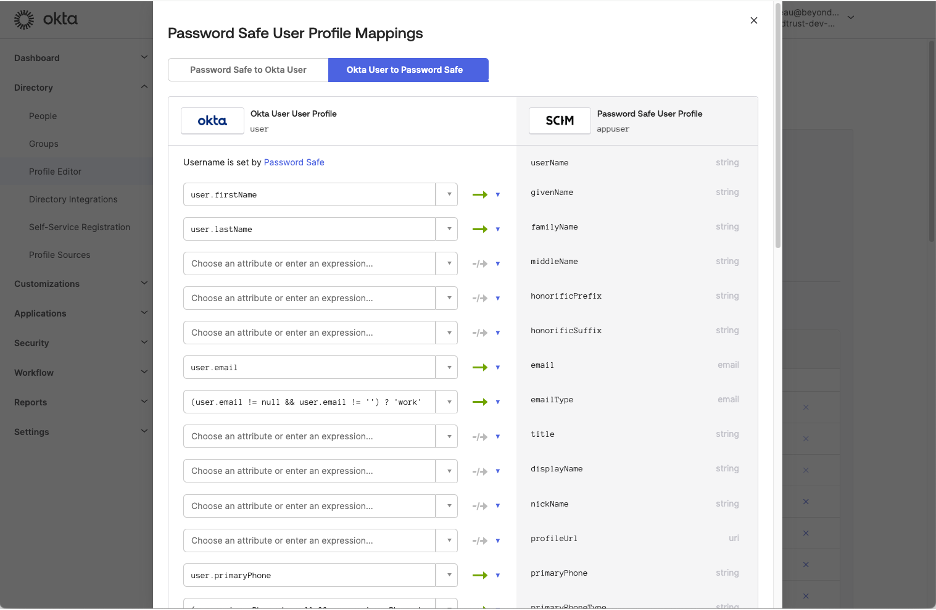
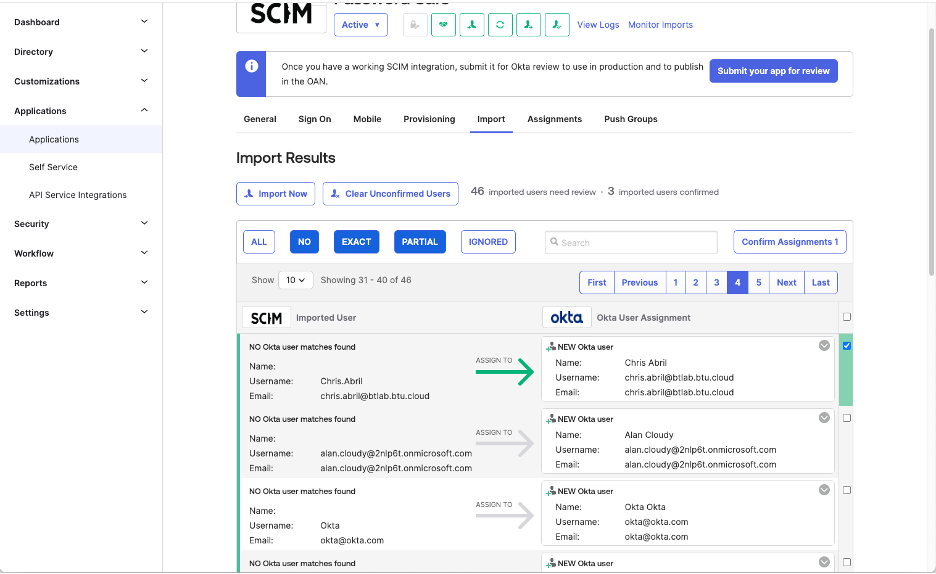
Supported Use Cases
Overview