Hello Everyone ,
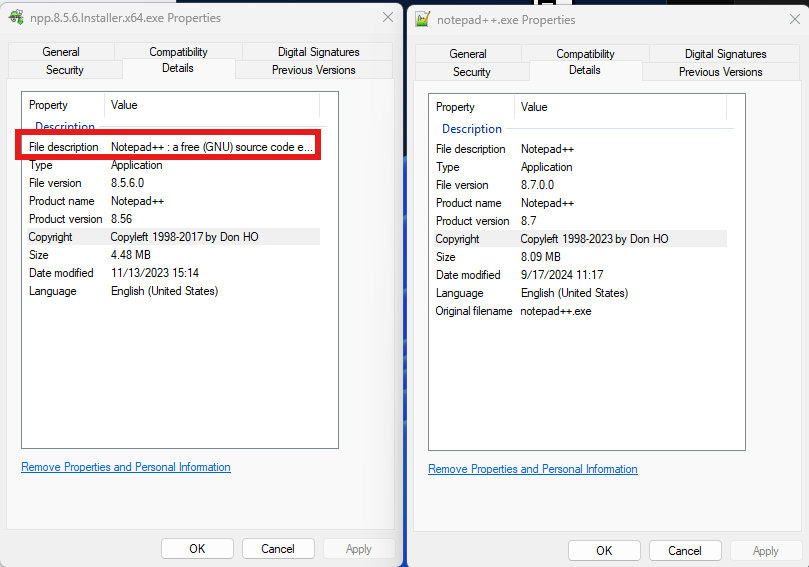
We would like to implement a policy that blocks the execution of an application if it is from an external source, even if it has the same publisher and version as one available in the Company Portal/Intune. However, the policy should allow the installation of the same application (with the same publisher and version) if it is from the Company Portal or Intune.
Our goal is to prevent the execution of any externally downloaded applications, while permitting installations from Intune or the Company Portal.
Example:
For Notepad++ version 8.7, the policy should block its execution if installed/downloaded from an external source, but allow installation if done through the Company Portal or Intune
Can this be achieved ?? if yes, how can this be implemented?
Appreciate in advance!!
Regards,
Suresh