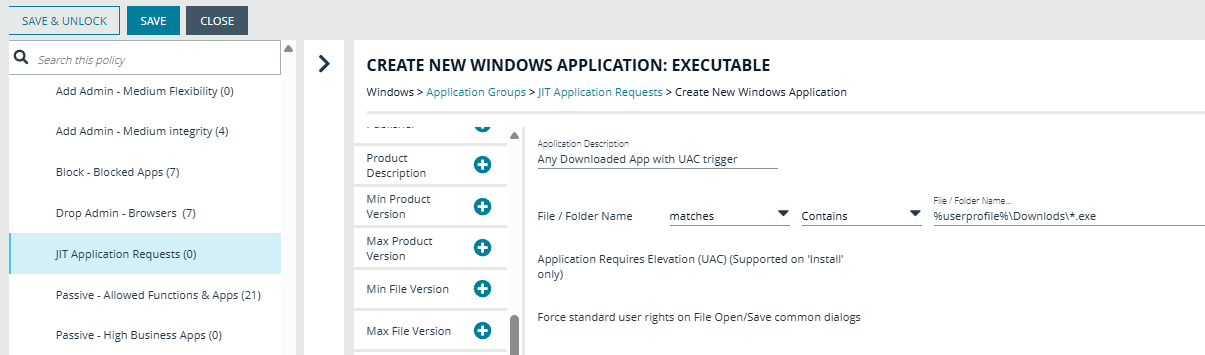
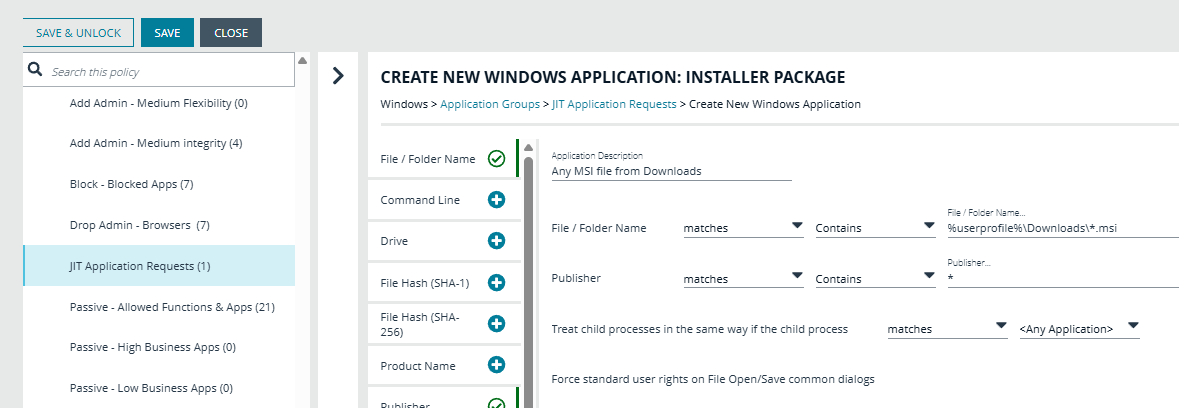
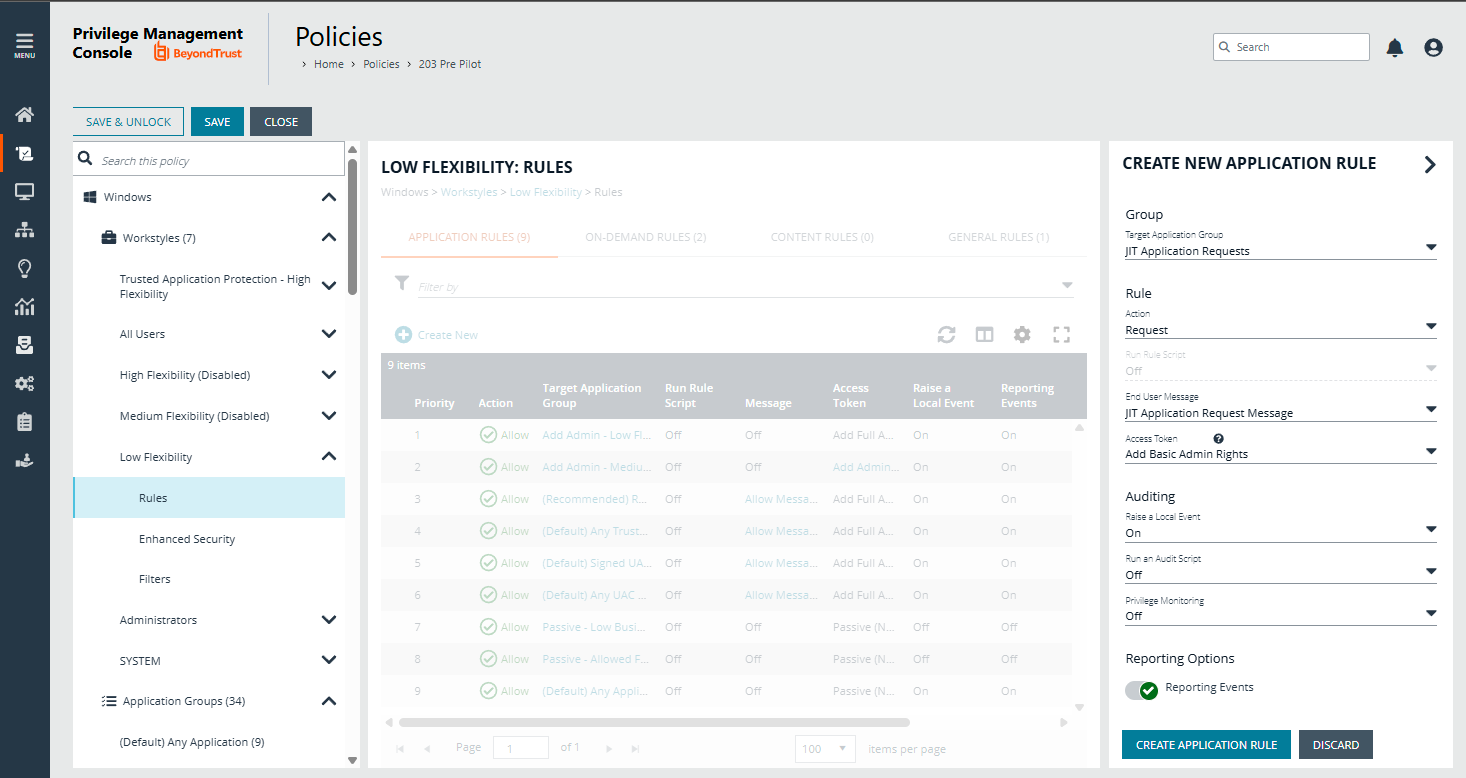
Is there any way to create an application group with JIT notification Only for application that requires Elevation( Target Audience: Standard user)?
Example scenario: If end user launches powershell under admin context then EPM should prompt them with JIT notification.