Hi guys, I’ve been assigned a case to block portable apps on a Windows desktop using EPM-W. What is the best way to target any portable apps on Windows? I have a portable application (FreeCommanderPortable.exe - this is just for testing, real-world apps can be anything) with the following criteria:
- It has a valid digital signature
- The .exe file can be originated from USB stick, internet download, or file sharing
- The .exe file can be moved to another folder/drive
- It doesn’t trigger UAC when run
- The file name can be changed to anything
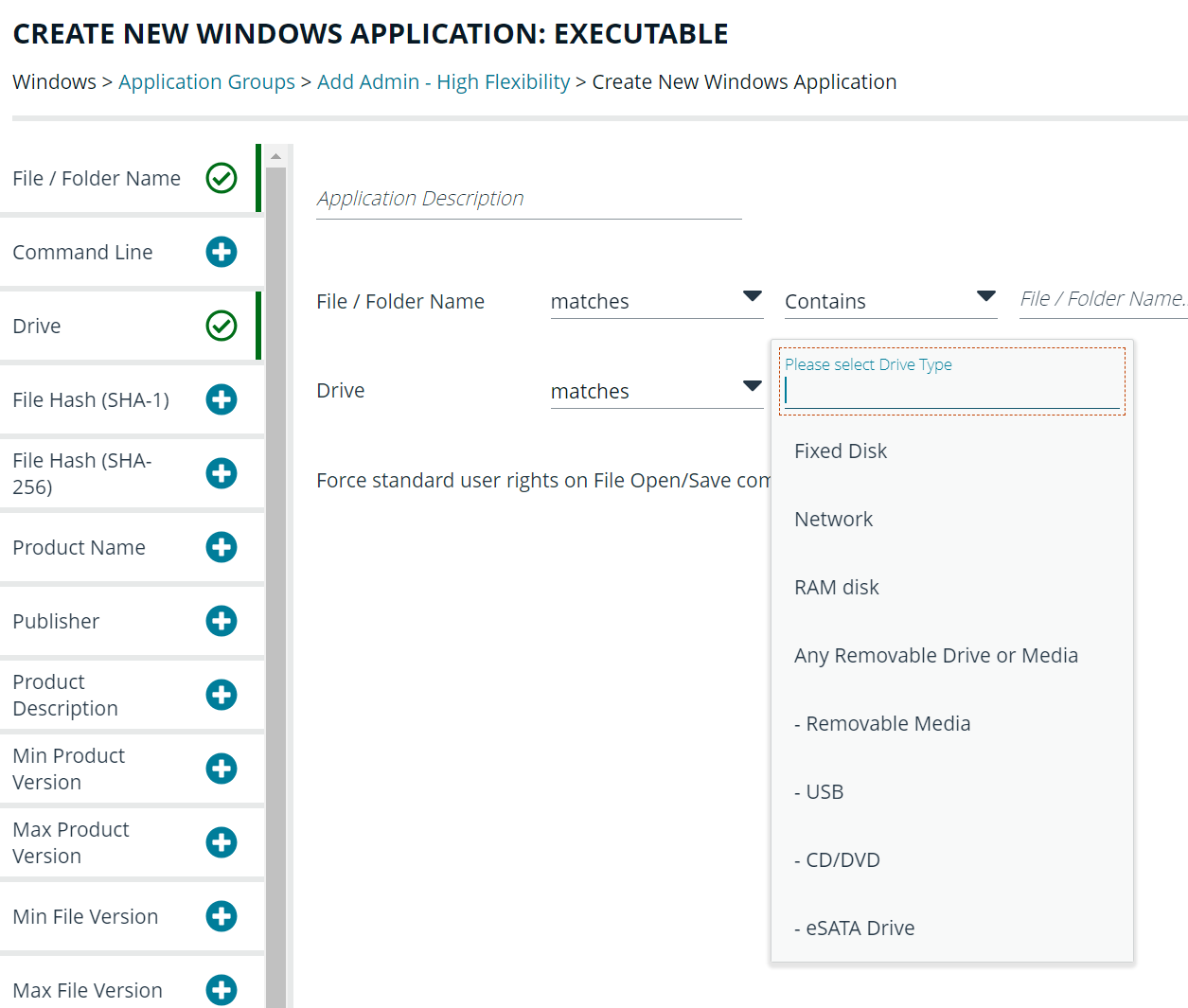
I tried creating an application group rule that targets any application ("*"), but there were many false positives, as some legitimate applications sometimes depend on each other.
The best configuration I can think of is to target if the publisher or the app name contains the string 'portable'. But not all portable applications have this string (e.g., if renamed).
Has anyone faced a similar scenario?