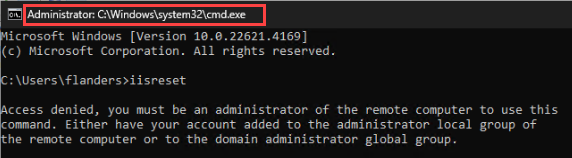
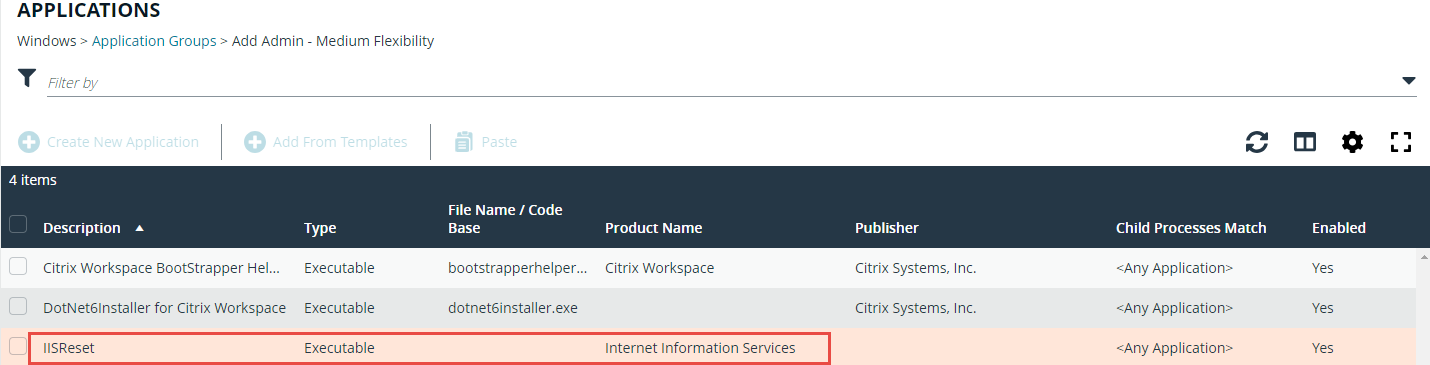
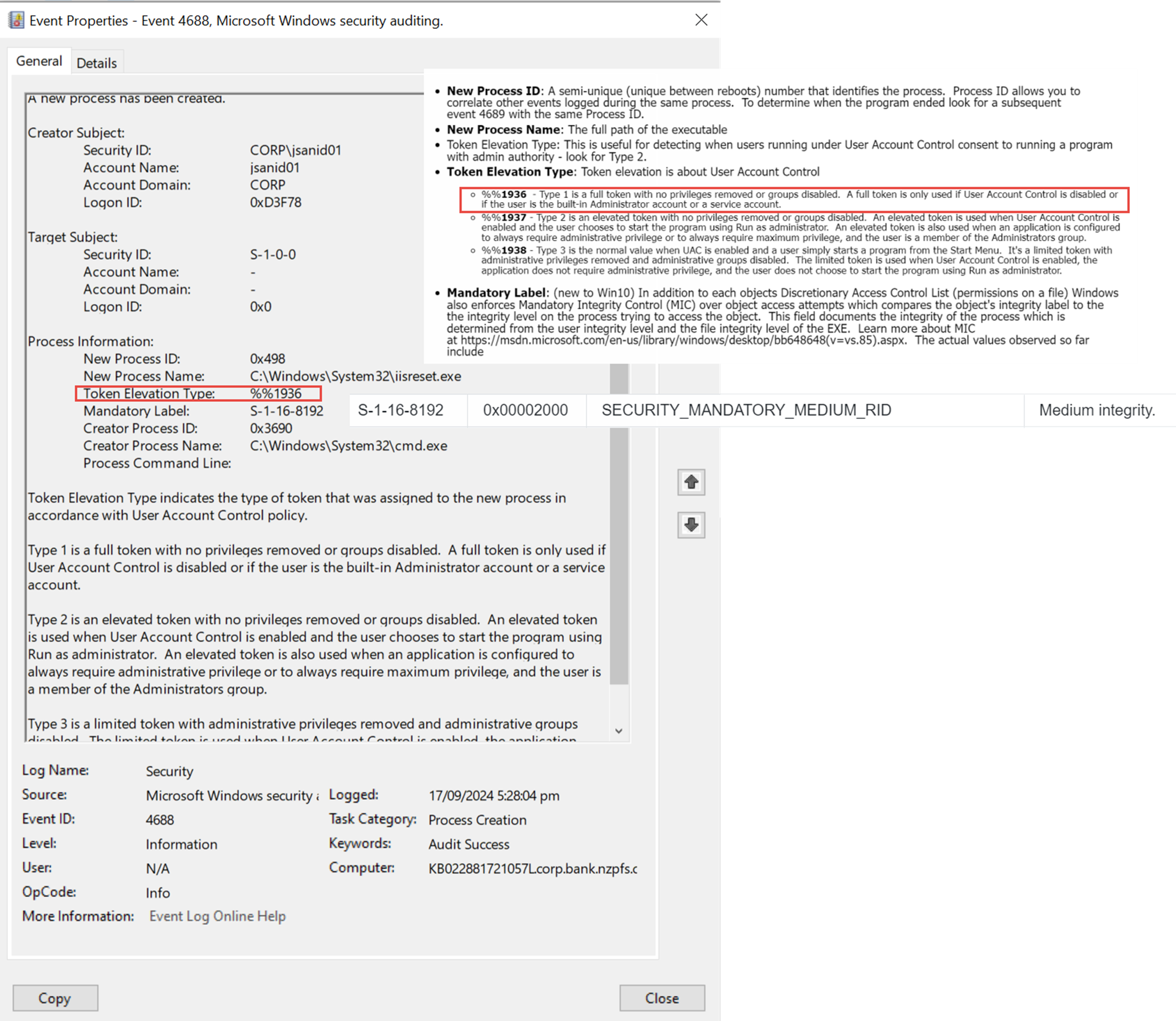
Anybody else encountered an issue with iisreset via commandline where the error coming up is “Access Denied” after running an elevated CMD?
Solved
iisreset.exe access denied error via elevated CMD
Best answer by Akshay Sharma
Hey
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.