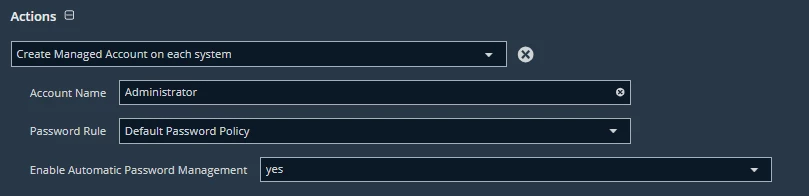
I’m working on a solution to onboard a local user account created during the Jamf provisioning of Mac assets to Password Safe Cloud. I have EPM-M installed on the endpoints and they are connected to Password Safe. When I run discovery scans on the endpoints, the local accounts are not discovered. I have looked over the KBs related, and nothing seems to explicitly say “Here is what you need to do” when it comes to local account management.
To test, I added a test functional account to the local admin group on a test Mac. This is an Active Directory service account, and it fails to login. As far as I can tell, the account needs to actually log into the Mac in order to be locally cached and thus login as a functional account. But having to locally log into each asset is not scalable. Has anyone had success with an AD group being used for your functional account? What am I missing to complete this set up?