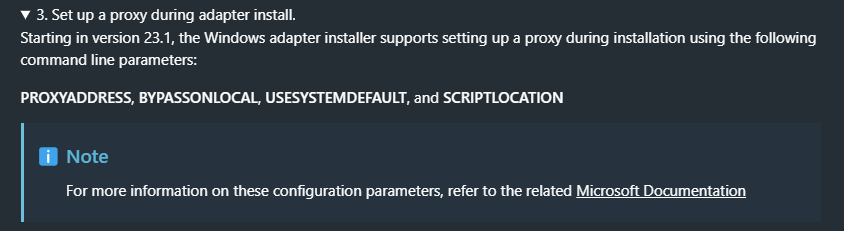
Does anyone know for the proxy settings for EPM described in https://beyondtrustcorp.service-now.com/csm?id=kb_article_view&sys_kb_id=ef0fc35b47534654b77b3ddbd36d43f8 , specifically the per user section, can a URL to a PAC file be used?
I saw another KB about configuring the local Windows system account to use a script based proxy. https://beyondtrustcorp.service-now.com/csm?sys_kb_id=455587d0476f02d4b77b3ddbd36d43d1&id=kb_article_view&sysparm_rank=3&sysparm_tsqueryId=e7573b9847582e5cb77b3ddbd36d439f
I think we’d prefer the first one as we know it will only affect the cloud adapter and not all services running as system.