Howdy folks,
It’s been a little over a week since the new JIT Admin feature was released and so I wanted to share a little bit of what I’ve learned while using it.
What is JIT Admin?
JIT Admin is a new feature in EPM (SaaS) 24.7, where a standard user can submit a JIT Admin request directly to the Privilege Management Console. Once approved, the standard user is put directly into the BUILTIN\Administrators group on their system, becoming a ‘true’ admin for a specified amount of time.
This feature is available on both Windows and Mac.
How do I enable JIT Admin?
I’ll add documentation at the bottom, but at a high level, enabling JIT admin requires three things:
- “JIT Admin Access Integration” is enabled under Configuration > Just-in-Time (JIT) Access Settings > Admin Access tab
- JIT admin is activated on a workstyle via policy OS > Workstyles > ellipses menu of the workstyle you want > Enable JIT Admin
- EPM 24.7+ on an endpoint
How can I start a JIT Admin session as an end user?
Note: this example is on Windows, but the process is quite similar for macOS.
A user can open their endpoint console app:
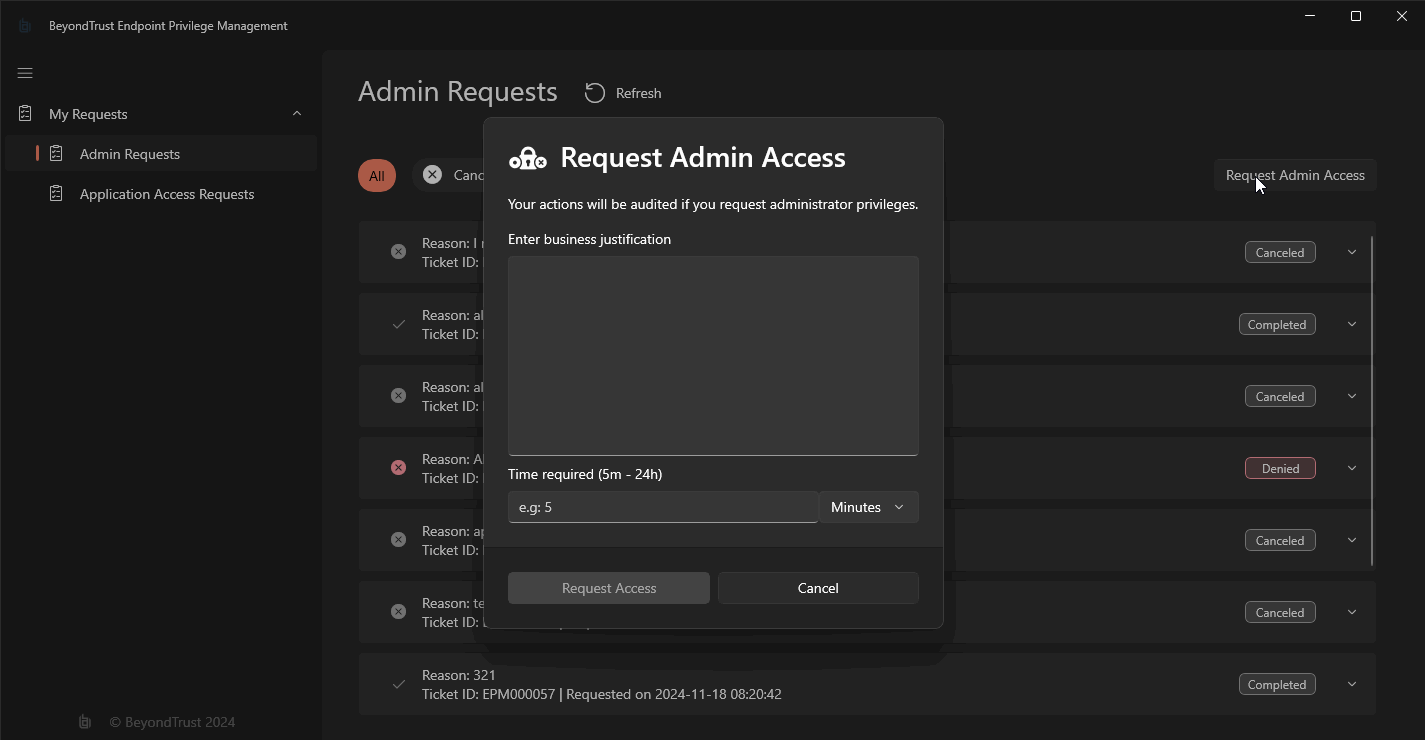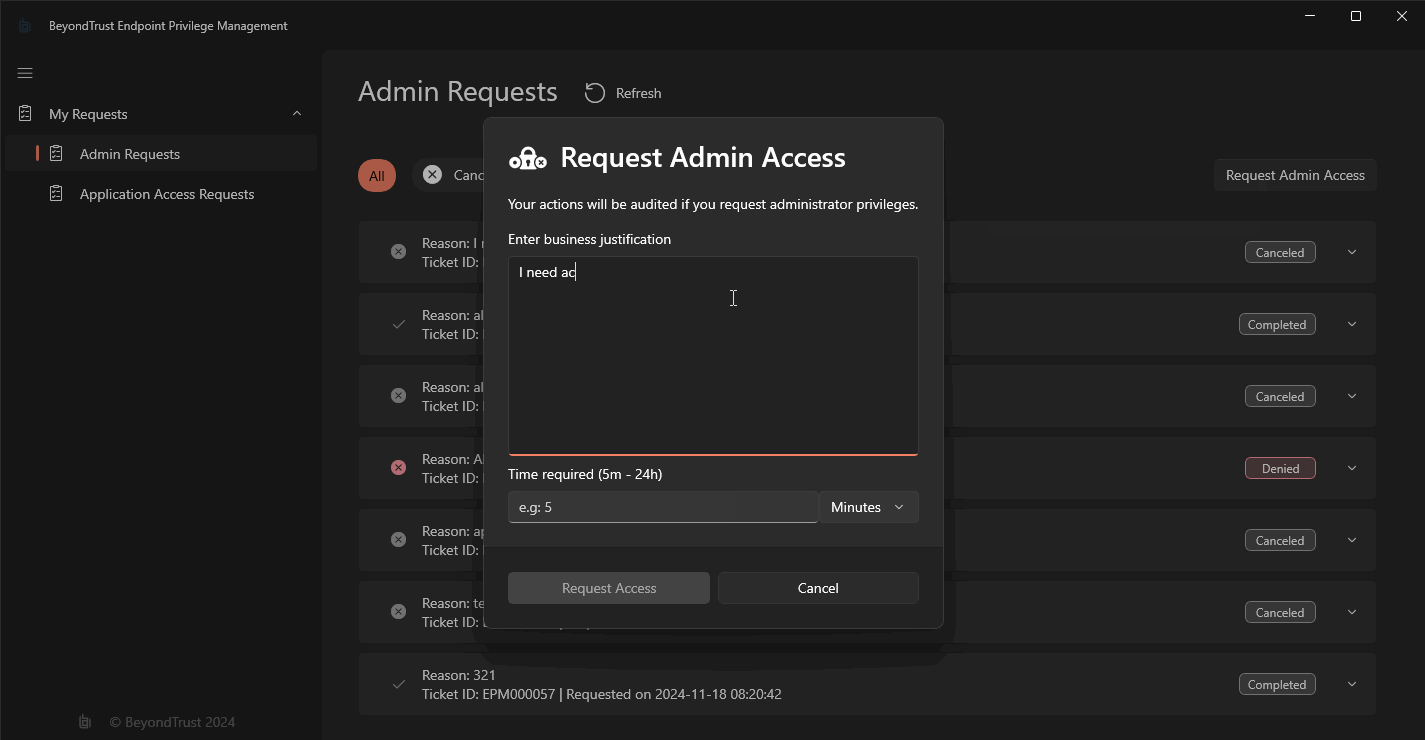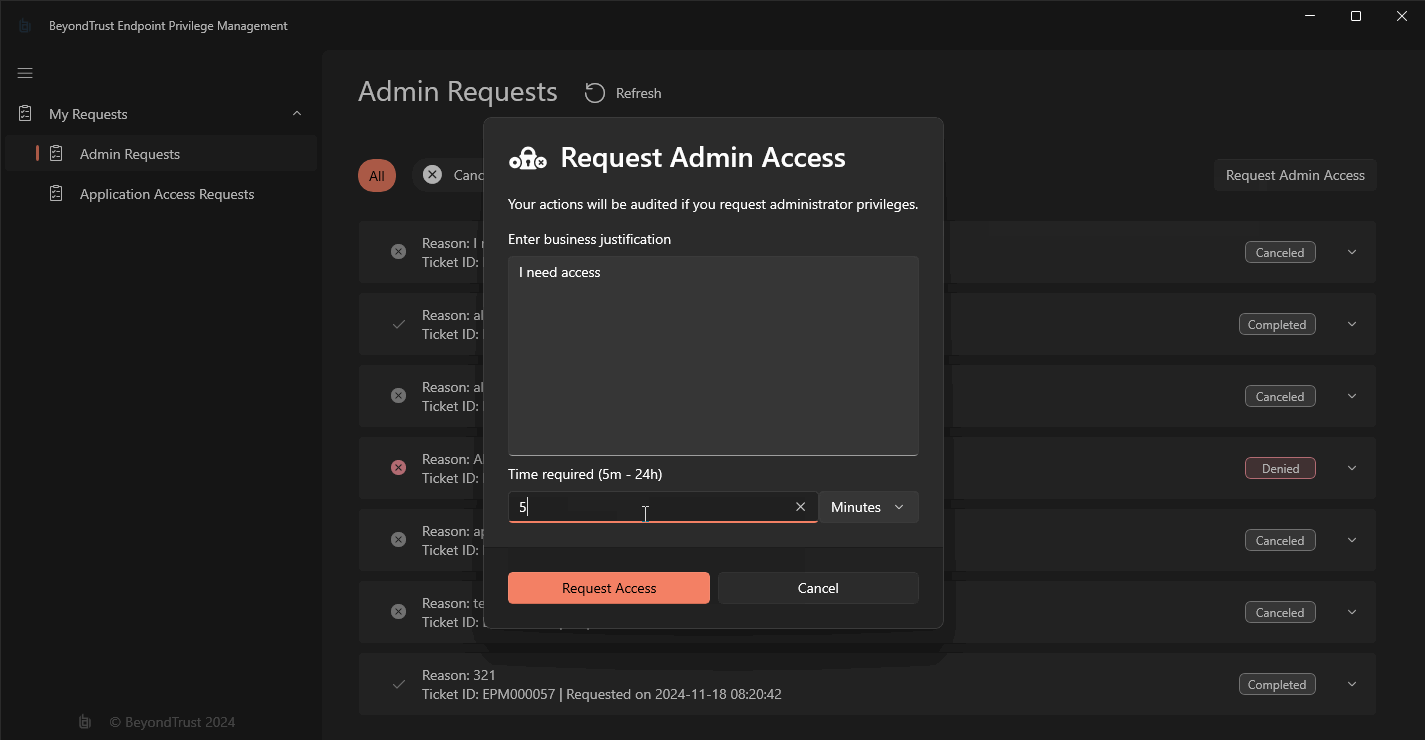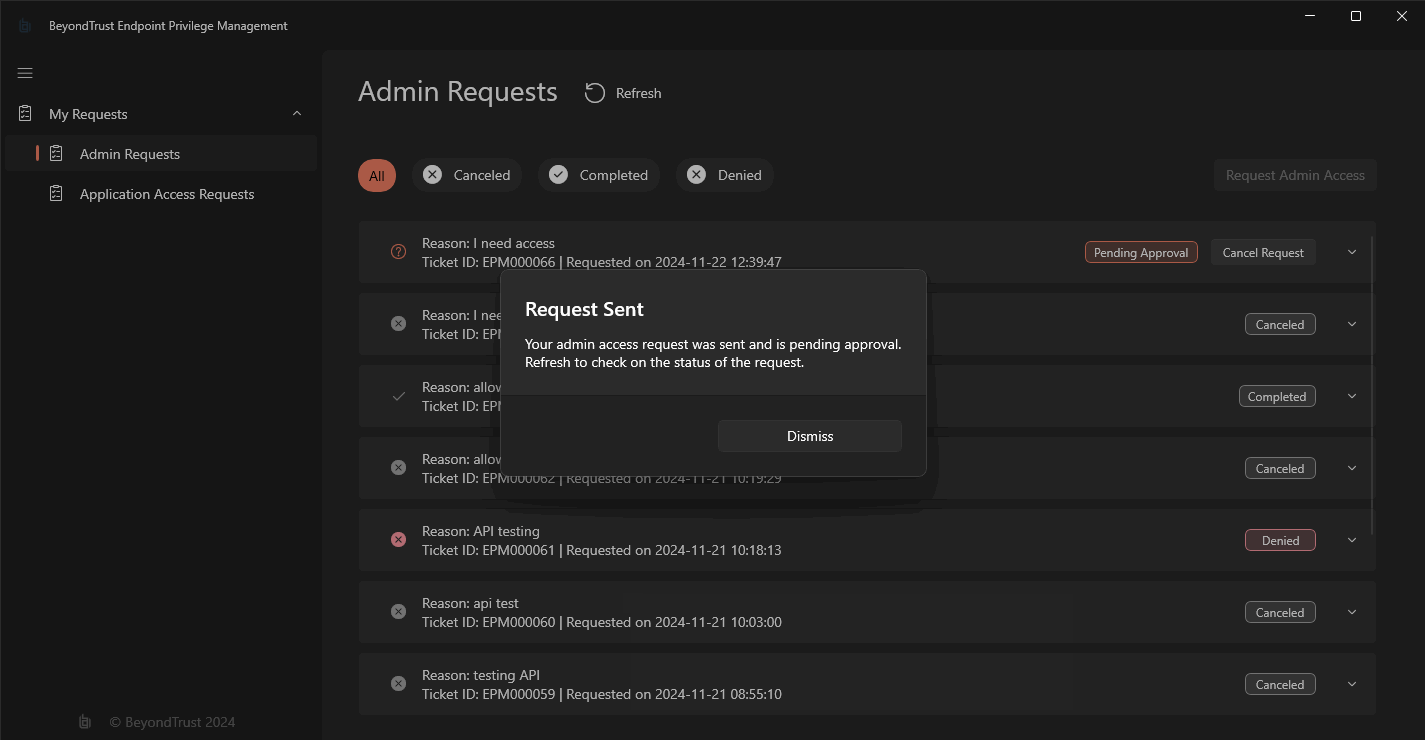
And if JIT Admin is enabled at the Workstyle level for them, they will be able to submit a request directly from the “Admin Requests” window:
Once the Request is allowed, the user can then start the JIT Admin session from the same window:
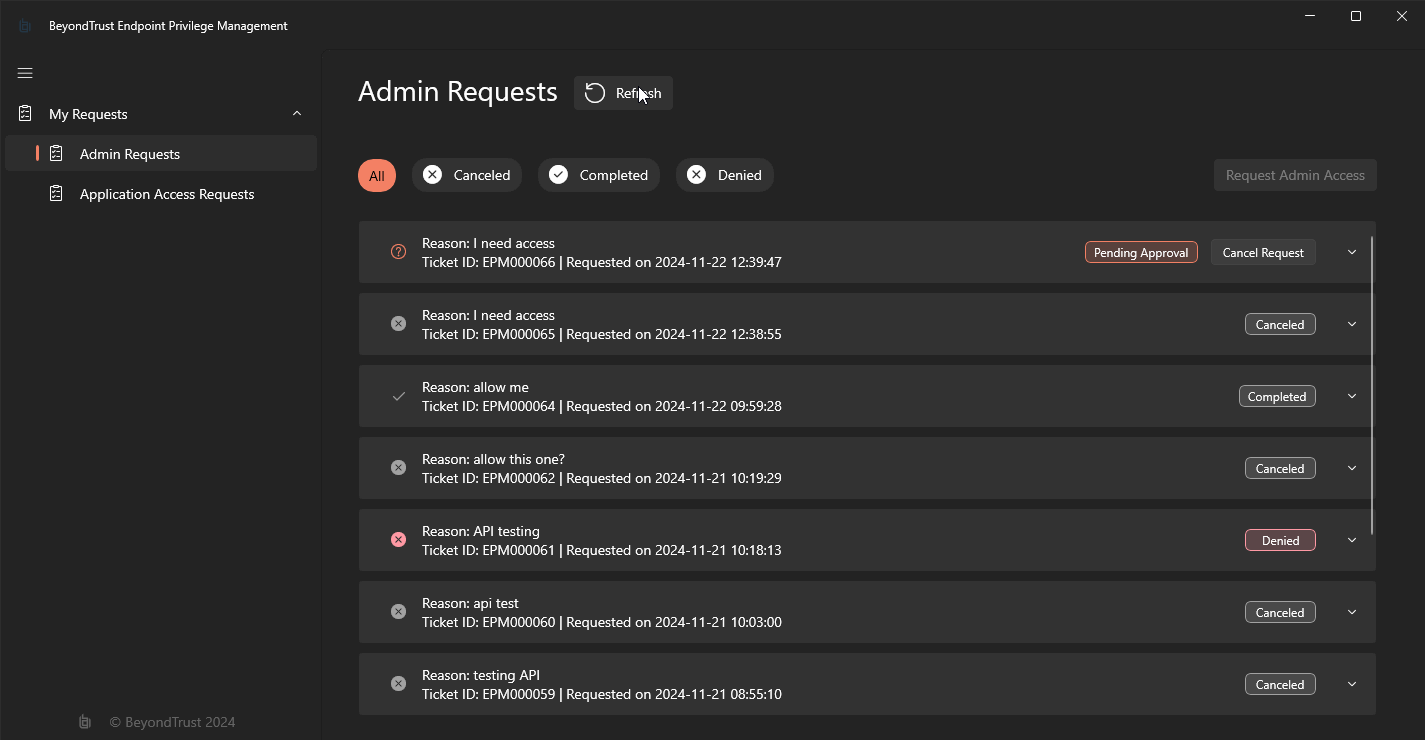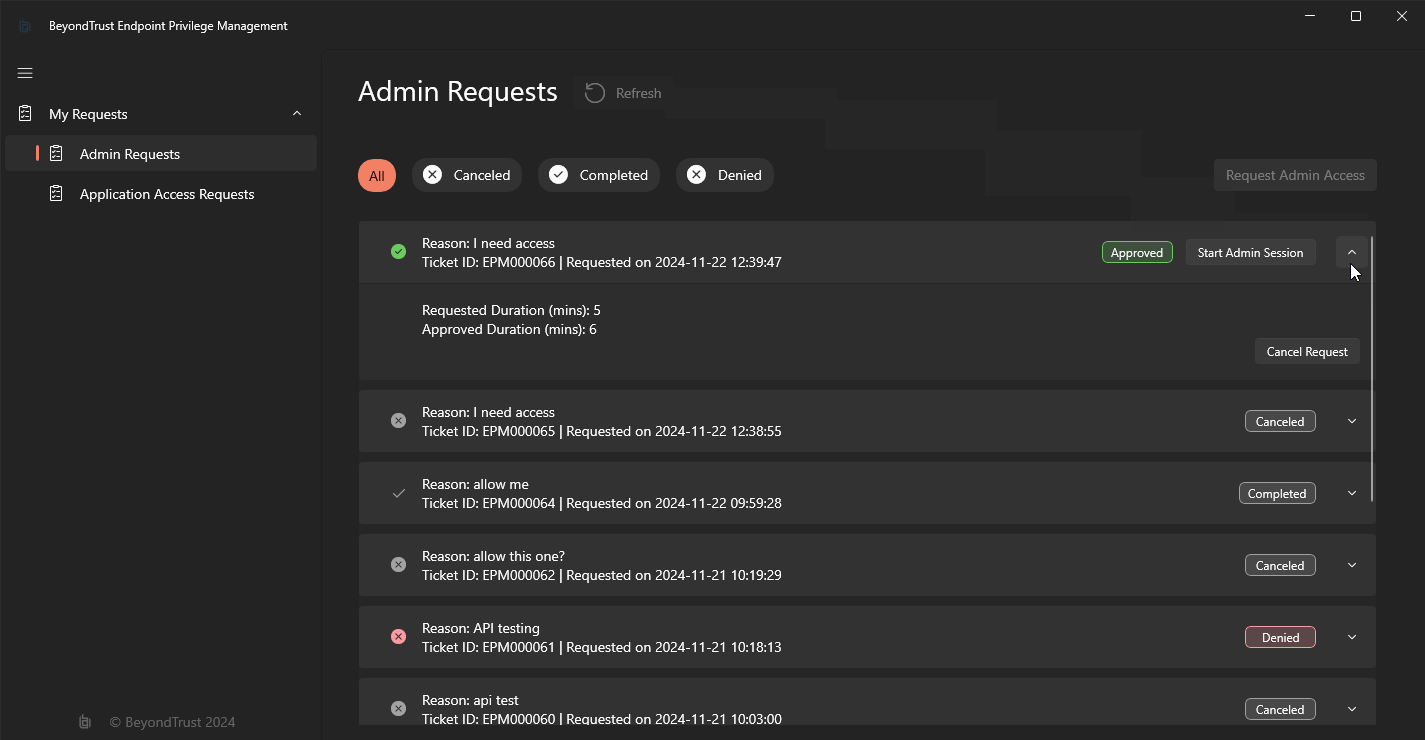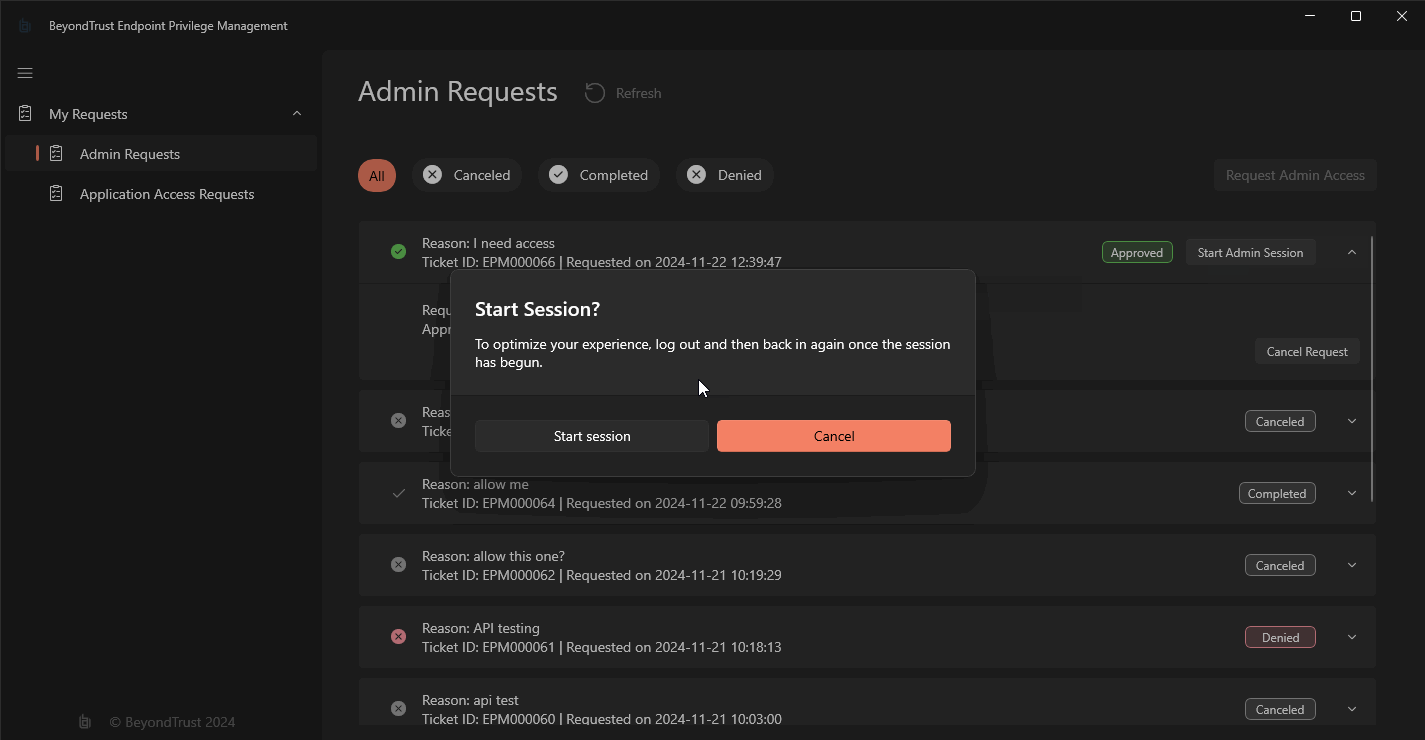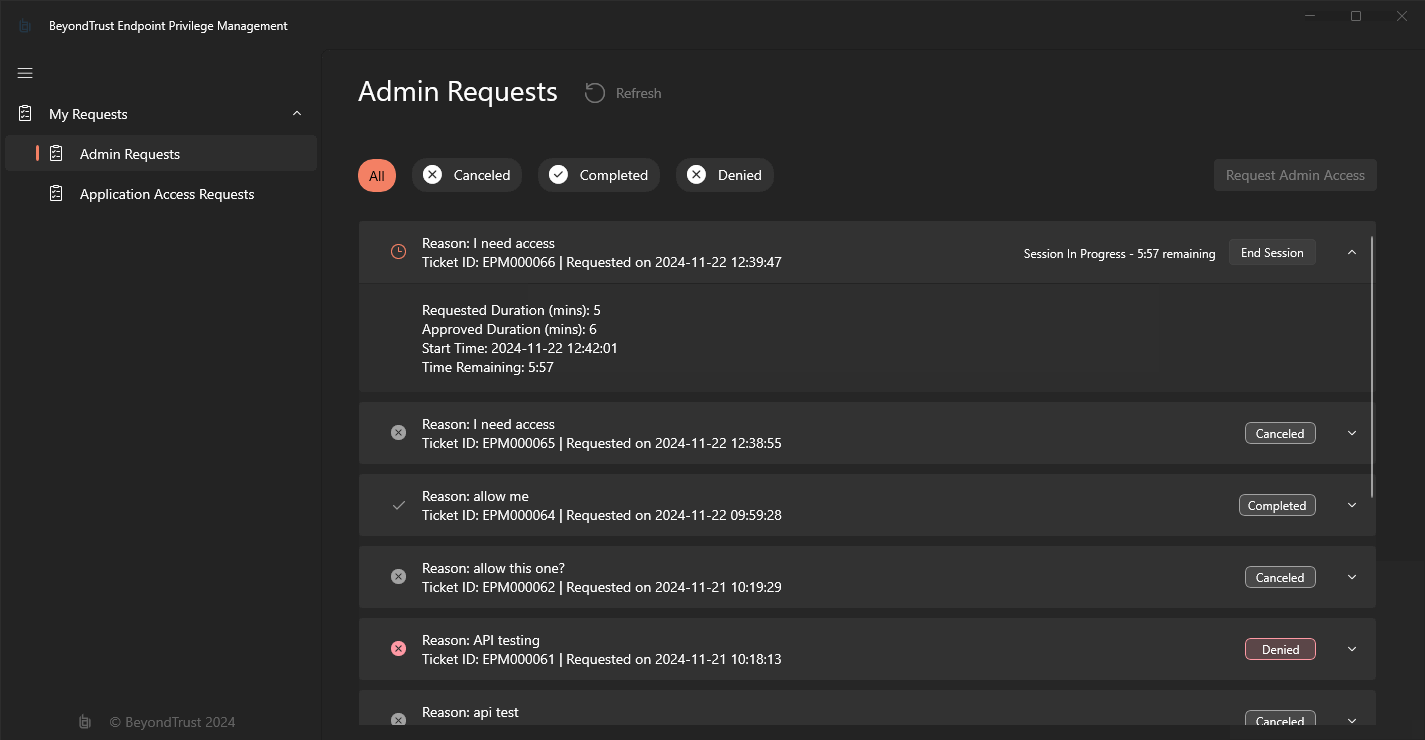
You can also control sessions via the EndpointUtility.exe:
What happens when my JIT Admin session ends?
When a JIT Admin session ends, the user must relog. When the session has 5 minutes remaining, a dialog box will pop up:
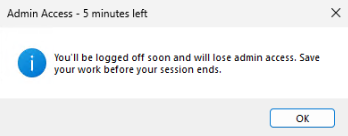
Why does a user have to log out? This is to make sure that all processes which were opened while in the Administrators group are closed.
What protections exist within a JIT Admin session?
All of EPM’s self-protection mechanisms, from Anti-Tamper to local privileged group protections, exist within a JIT admin session. What this means is that while I’m in a JIT Admin session, I may be a member of the BUILTIN\Administrators group, but I still cannot:
- Disable EPM services
- Modify protected EPM directories / registry locations / etc.
- Uninstall EPM
- Create rogue admin users
How are JIT Admin sessions audited?
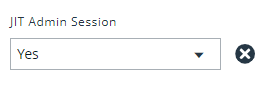
All elevations and blocks are audited completely. Within Analytics, you can filter specifically on JIT Admin session events:
Or on a specific ticket number itself:
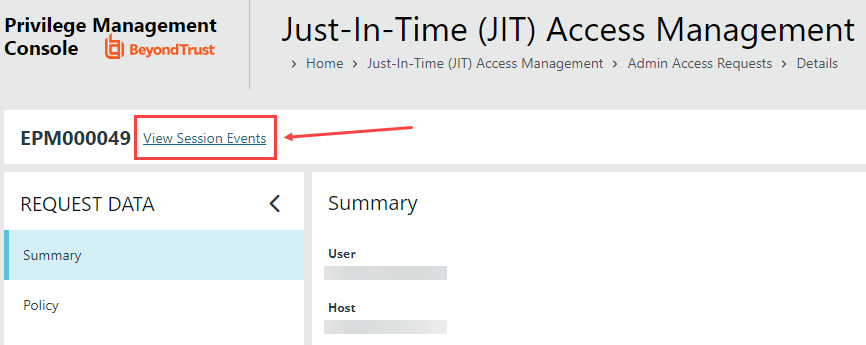
One awesome feature is that you can get to a specific JIT Admin session’s events from the Just-In-Time (JIT) Access Management page (where you approve/deny requests). If you filter on “In Progress” sessions, click into one of them, there will be a link to “View Session Events” that you can watch unfold in near real-time:
You can likewise do this with “Completed” JIT Admin sessions.
What are some use cases for JIT Admin?
I’m mostly hoping to hear from y’all what some of the use-cases you can come up with are, but the main ones I’ve seen are:
- Handling hard checks of the BUILTIN\Admin group
Surprisingly often I come across applications or installers which do not rely on Windows UAC, but instead perform hard-coded checks of BUILTIN\Admin group membership. I mostly see this with legacy software installers, certain driver installers, that type of thing. For Mac, this would be something like the Console.app, where you must be an admin in order to use it. Typically, there is no way around this other than truly being a member of the Admin group; with JIT Admin, however, we’ll be able to handle these hard checks a bit more gracefully.
- Troubleshooting
Mostly self-explanatory :)
- Onboarding new users
Example: You’ve got a newly hired developer who needs to set up their lab environment and install various software in order to do their job. Using a JIT Admin session for a few hours might serve as a nice ‘grace period’ for allowing them to install the tools they need (while being audited) without having to jump through EPM prompts.







